I remember a late night debugging session where a mysterious data corruption bug turned out to be a poorly implemented encryption routine. It was a painful lesson: good encryption is not just about security, it is about system reliability and building trust. We often treat encryption as a complex, arcane topic reserved for security specialists, but for a modern startup, it is as fundamental as your database choice. Getting it wrong can lead to catastrophic data breaches, regulatory fines, and a complete loss of user confidence. Getting it right means building a resilient, trustworthy product from the ground up.
This article is not a dry academic paper. It is a field guide, a journey through the 10 data encryption best practices I have learned to lean on when building production grade systems. We will move from the 'what' to the 'why' and finally to the 'how,' exploring the trade offs, the gotchas, and the practical steps needed to protect your users' data and your company's reputation. To grasp the foundational importance of this topic, begin by exploring understanding the role of encryption in information security before we dive into the specific tactics.
We will cover everything from selecting strong algorithms and managing keys with cloud KMS services to the nuances of encrypting data at rest versus in transit. We will look at concrete examples for Django and Python environments, discuss the security of JWTs, and even touch on encryption strategies for modern RAG systems. This is your roadmap to implementing a robust, scalable, and secure encryption strategy. Let's level up together.
1. Use Strong Encryption Algorithms
The foundation of any robust data encryption strategy is the choice of algorithm. Think of it like the lock on a vault; using a weak, outdated lock is like inviting trouble, no matter how thick the vault walls are. Selecting a cryptographically secure and internationally recognized algorithm is a non negotiable first step, representing one of the most critical data encryption best practices.
What Makes an Algorithm "Strong"?
Strong algorithms are those that have undergone extensive public scrutiny and rigorous cryptanalysis by the global security community. They have no known practical vulnerabilities that would allow an attacker to break the encryption in a reasonable timeframe. The gold standard for symmetric encryption (where the same key is used to encrypt and decrypt) is AES 256 (Advanced Encryption Standard with a 256 bit key). For asymmetric encryption (using a public key to encrypt and a private key to decrypt), algorithms like RSA 2048 and Elliptic Curve Cryptography (ECC) are the trusted choices.
These are not arbitrary selections; they are battle tested standards. For instance, AES 256 is trusted by the U.S. government to protect classified information. Cloud providers like AWS use it by default for services like S3 server side encryption, and the entire banking sector has standardized on AES for securing financial transactions.
Actionable Tips for Implementation
When implementing these algorithms, a few rules of thumb will keep you secure:
- Always Use Full Key Strength: If you choose AES 256, ensure you are using the full 256 bit key. Using a shorter key weakens the encryption significantly.
- Avoid Proprietary or Deprecated Algorithms: Steer clear of custom, in house encryption or older standards like DES or MD5. They often contain hidden flaws or have been publicly broken. Stick to algorithms vetted by institutions like NIST (National Institute of Standards and Technology).
- Prioritize Authenticated Encryption: Whenever possible, use an authenticated encryption mode like AES GCM (Galois/Counter Mode). This mode not only encrypts the data but also provides integrity and authenticity checks, protecting against tampering and forgery attacks.
2. Implement Proper Key Management
If your encryption algorithm is the lock, your cryptographic key is the one and only thing that opens it. A compromised key renders even the strongest encryption completely useless. This is why proper key management is not just a suggestion; it is an absolutely critical component of any data encryption best practices, arguably more complex and prone to error than choosing the algorithm itself.
What Makes Key Management "Proper"?
Proper key management encompasses the entire lifecycle of a key: its secure generation, storage, usage, rotation, and eventual destruction. It's about treating your keys like the ultimate secrets they are. A robust strategy ensures keys are never exposed in plaintext in logs, code, or configuration files and that access is strictly controlled. For a deeper look into the mechanics of cryptographic keys, an excellent primer on the difference between public and private keys can clarify their distinct roles.
The modern standard for this is using dedicated services like a Key Management Service (KMS) or a Hardware Security Module (HSM). Cloud providers like AWS KMS and Google Cloud KMS handle the difficult parts of the key lifecycle for you, including generation from certified hardware random number generators and automated rotation. This approach separates your keys from your application data, a fundamental security principle. Learn more about the fascinating world of symmetric vs asymmetric encryption keys and how they work.
Actionable Tips for Implementation
To build a resilient key management system, focus on these core principles:
- Centralize Key Storage: Use a dedicated and audited system like AWS KMS, Azure Key Vault, or HashiCorp Vault. Never, ever store encryption keys directly in application code, environment variables, or databases.
- Enforce Least Privilege: Grant permissions to use keys, not access them directly. Your application should have the IAM role to use a key for an operation (encrypt/decrypt), but not to read the key material itself.
- Automate Key Rotation: Regularly rotating keys limits the "blast radius" if a key is ever compromised. Set up automated, periodic rotation policies (e.g., annually) within your KMS. This is a key part of compliance with standards like PCI DSS.
- Separate Keys by Purpose: Use different keys for different services, data types, or environments (e.g., one for user PII, another for application secrets). This compartmentalization prevents a single key compromise from exposing all your encrypted data.
3. Enable End to End Encryption (E2EE)
While encrypting data at rest and in transit protects it from many threats, End to End Encryption (E2EE) offers the ultimate layer of privacy. This approach ensures that data is encrypted on the sender's device and can only be decrypted by the intended recipient. No one in between, not even the service provider or platform operator, can access the unencrypted information. For applications handling deeply sensitive communications, implementing E2EE is one of the most powerful data encryption best practices you can adopt.
What Makes E2EE So Secure?
The core principle of E2EE is that the service provider never holds the decryption keys. Keys are generated and stored exclusively on user devices. When a user sends a message, it is encrypted locally before being transmitted, and it remains encrypted until it reaches the recipient's device for decryption. This model eliminates the risk of server side data breaches exposing sensitive content.
The gold standard in this space is the Signal Protocol, developed by Moxie Marlinspike and used by apps like Signal and WhatsApp. It provides confidentiality, integrity, and authenticity, as well as forward secrecy and post compromise security. This means even if a user's long term key is compromised, past and future messages remain secure. Other examples include ProtonMail for email and optional E2EE modes in Microsoft Teams for calls.
Actionable Tips for Implementation
Implementing E2EE is a complex endeavor, but following proven patterns is key:
- Implement a Vetted Protocol: Do not attempt to build your own E2EE protocol. Instead, use a well audited and widely trusted implementation like the Signal Protocol. This gives you a battle tested foundation to build upon.
- Use Ephemeral Keys for Forward Secrecy: Ensure your implementation uses ephemeral (short lived) session keys. This crucial feature guarantees that if a key is ever compromised, only a very small amount of data is at risk, protecting past communications.
- Provide Secure Key Verification: Users need a way to verify they are communicating with the correct person. Implement out of band verification methods like safety number comparisons or QR code scanning to protect against man in the middle attacks.
4. Use Authenticated Encryption Modes
Simply encrypting data is not always enough to guarantee security. Imagine you encrypt a message, "Pay Alice $100," and an attacker intercepts it. Even without knowing the key, they could potentially flip specific bits in the ciphertext. When you decrypt it, the message might now read "Pay Mallory $900," and your system would have no way of knowing it was altered. This is where authenticated encryption comes in, and it is a non negotiable part of modern data encryption best practices.
What Is Authenticated Encryption?
Authenticated Encryption with Associated Data (AEAD) is a type of encryption that simultaneously provides confidentiality, integrity, and authenticity. It bundles encryption with a message authentication code (MAC). This means not only is the data unreadable without the key, but any modification to the ciphertext will be detected during decryption, causing the process to fail. The most widely adopted and recommended modes are AES GCM (Galois/Counter Mode) and ChaCha20 Poly1305.
These modes are the backbone of modern secure communication. TLS 1.3, the latest standard for web traffic, exclusively uses AEAD ciphers. The fast and modern VPN protocol WireGuard relies on ChaCha20 Poly1305 for its security. Even physical security keys following the FIDO2 standard use authenticated encryption to protect credentials. This approach ensures that the data you decrypt is the exact same data that was originally encrypted.
Actionable Tips for Implementation
To implement authenticated encryption correctly, you need to manage more than just the key:
- Default to AES GCM: For most applications, AES GCM is the gold standard. It's hardware accelerated on most modern processors, making it both secure and highly performant.
- Never Reuse a Nonce: The "Number used once" (nonce) is critical. Reusing a nonce with the same key completely breaks the security of GCM and other modes. Always generate a random, sufficiently long nonce for every single encryption operation.
- Leverage Associated Data: AEAD allows you to include additional, unencrypted "associated data" (AAD) in the authentication check. This is useful for binding metadata, like a user ID or a timestamp, to the ciphertext, ensuring it cannot be tampered with or replayed in a different context.
- Use High Level Libraries: Avoid implementing cryptographic primitives yourself. Instead, use a battle tested library like libsodium or the cryptography primitives within your cloud provider's SDK. These libraries handle complex details like nonce generation and tag verification safely.
5. Encrypt Data at Rest, in Transit, and in Use
Data is not static; it flows through your systems like a current, existing in different states at different times. A common mistake is to protect it in one state while leaving it exposed in another. Truly comprehensive security, and a cornerstone of data encryption best practices, demands that you protect data throughout its entire lifecycle: when it is stored, when it is moving, and even when it is being processed.
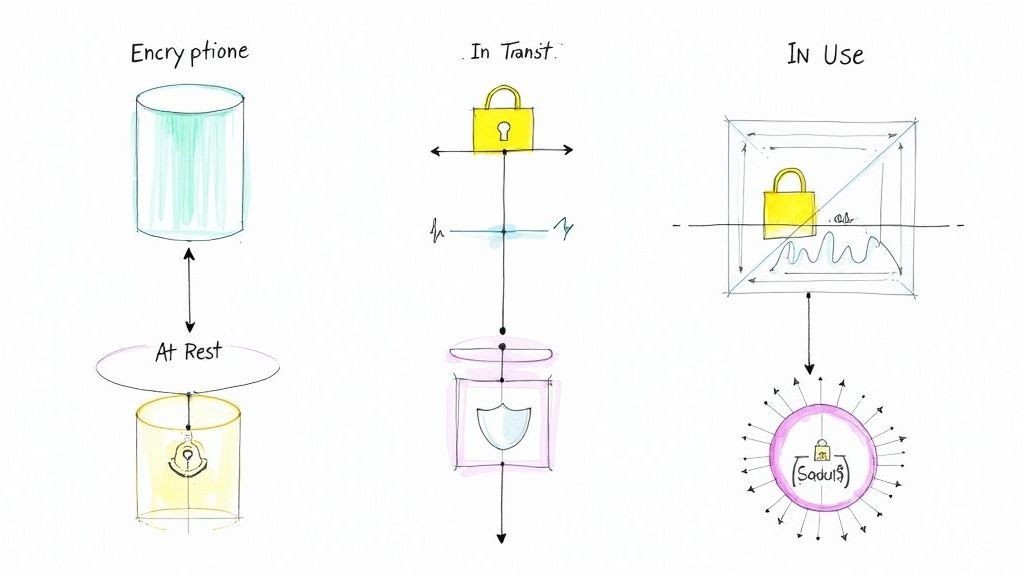
What Do These States Mean?
Think of it as a three layer defense. Encrypting data at rest protects your stored data on hard drives, in databases, or in cloud storage like Amazon S3 from physical theft or unauthorized access. Encrypting data in transit secures it as it travels across networks, like the internet or internal APIs, preventing eavesdropping. Finally, encrypting data in use, the newest frontier, protects data while it is in active memory (RAM) being processed by an application.
Major platforms live by this rule. Google Cloud, for example, automatically encrypts all data at rest and in transit between its facilities. Salesforce offers Platform Encryption to secure sensitive data at rest in specific fields. This multi state approach ensures there are no gaps for an attacker to exploit, whether they breach a server, intercept network traffic, or attempt a memory scraping attack. Understanding this is key, just as it is vital to distinguish between core cryptographic concepts; explore how encryption differs from hashing in this story driven guide.
Actionable Tips for Implementation
To apply this three pronged strategy effectively, you need a holistic view of your data flows:
- For Data at Rest: Use Transparent Data Encryption (TDE) for databases like PostgreSQL or SQL Server. For object storage, always enable server side encryption features provided by your cloud provider, such as AWS S3's SSE KMS.
- For Data in Transit: Mandate TLS 1.3 for all client server communication, APIs, and internal service calls. Configure your web servers and load balancers to reject older, insecure protocols.
- For Data in Use: This is more advanced, but explore confidential computing technologies like AWS Nitro Enclaves or Google Confidential Computing. These create isolated, encrypted memory regions where sensitive data can be processed securely, keeping it hidden even from the host system.
6. Implement Perfect Forward Secrecy (PFS)
Imagine a scenario where a master key to your entire communication history is stolen. With traditional encryption, this single breach could allow an attacker to retroactively decrypt every message you have ever sent. This is where Perfect Forward Secrecy (PFS) comes in, acting as a critical firewall between past, present, and future communications. It is an essential component of modern data encryption best practices, ensuring that a compromise of long term keys does not compromise past session data.
What is Perfect Forward Secrecy?
Perfect Forward Secrecy is a property of secure communication protocols where a compromise of long term keys does not compromise past session keys. Instead of using one static key to protect all data, PFS protocols generate a unique, temporary session key for each individual conversation. Once the session ends, that key is destroyed and never used again. This is typically achieved using an ephemeral Diffie Hellman key exchange, most commonly Elliptic Curve Diffie Hellman Ephemeral (ECDHE).
The practical impact of this is enormous. Even if an attacker records all your encrypted traffic for years and later manages to steal your server's private key, they still cannot decrypt any of that historical data. Each session was protected by its own unique, discarded key. This is why TLS 1.3 now mandates PFS, and it is the core principle behind secure messaging apps like Signal and WhatsApp.
Actionable Tips for Implementation
To effectively implement PFS, focus on your protocol configurations and verification:
- Configure Your Web Server Correctly: For TLS, ensure your server is configured to prioritize cipher suites that use ECDHE. Explicitly disable outdated static RSA key exchange ciphers, which do not provide forward secrecy.
- Use Strong Elliptic Curves: When using ECDHE, choose modern, secure curves like
X25519for the best balance of security and performance. Avoid older, weaker, or potentially compromised curves. - Verify Your Configuration: Do not just assume PFS is working. Use free online tools like the SSL Labs SSL Test to scan your public facing endpoints. The test will confirm whether you have forward secrecy enabled and highlight any configuration weaknesses.
- Destroy Session Keys: Ensure your application or system securely and promptly destroys session keys after a session is terminated. This is fundamental to the security model of PFS. For more on future proofing your encryption, you can learn more about how quantum computing could reshape digital privacy.
7. Use Secure Transport Protocols (TLS 1.3+)
While encrypting data at rest is crucial, that protection is meaningless if the data is exposed during transit. Encrypting data in transit protects it from eavesdropping and man in the middle attacks as it moves across networks. This is where Transport Layer Security (TLS) becomes a cornerstone of any security posture, and a mandatory data encryption best practices implementation.
What Makes TLS 1.3 a Game Changer?
TLS 1.3 is not just an incremental update; it is a significant security overhaul. It streamlines the connection handshake, making it faster and more secure by encrypting more of the initial communication. Crucially, it removes support for outdated and vulnerable cryptographic primitives, such as weak ciphers and insecure hashing algorithms like SHA 1 and MD5. This modern protocol is the standard for major technology platforms; Google services, the Apple ecosystem, and all modern web browsers enforce or prioritize TLS 1.3 for its superior security guarantees.
This is not just about web traffic. Any service that communicates over a network, from database connections to internal microservice API calls, must be secured with a strong TLS configuration. Failing to protect this "in flight" data is like sending a sealed letter in a transparent envelope.
Actionable Tips for Implementation
To properly secure data in transit, you must be rigorous with your TLS configuration:
- Disable Legacy Protocols: Actively disable all versions of SSL, TLS 1.0, and TLS 1.1 on your servers. Even TLS 1.2 should be phased out wherever possible to eliminate its weaker cipher suites.
- Enforce Strong Cipher Suites: Configure your servers to only accept modern, authenticated encryption ciphers. For TLS 1.3, this includes suites like TLS_AES_256_GCM_SHA384 and TLS_CHACHA20_POLY1305_SHA256.
- Implement HTTP Strict Transport Security (HSTS): Use the HSTS header to instruct browsers to only communicate with your domain over HTTPS, preventing protocol downgrade attacks.
- Configure OCSP Stapling: Improve performance and privacy by having your server "staple" the certificate validation response from the Certificate Authority (CA), preventing the client's browser from having to make a separate request.
8. Implement Regular Key Rotation and Updates
Even the strongest encryption key has a shelf life. An encryption key is a single point of failure; if it is compromised, all data it protects becomes vulnerable. Regular key rotation is the practice of retiring an old key and replacing it with a new one, drastically limiting the "blast radius" of a potential compromise. This process is a cornerstone of modern security hygiene and one of the most impactful data encryption best practices.
What Makes Rotation "Effective"?
Effective key rotation is not just about changing keys; it is about doing so systematically, automatically, and safely. The goal is to minimize the window of opportunity for an attacker. If a key is compromised but was only in use for 90 days, the attacker's access is limited to data from that period. Without rotation, a single compromised key could grant access to years of sensitive information.
Cloud providers have made this process incredibly accessible. AWS KMS and Google Cloud KMS both offer automated key rotation policies, where a new cryptographic key is generated on a set schedule (typically annually) without any manual intervention. This automation is crucial, as it removes the potential for human error or forgetfulness. For highly sensitive data, like in the banking sector, quarterly rotation is a common mandate.
Actionable Tips for Implementation
Properly implementing a rotation strategy requires careful planning to avoid service disruptions:
- Automate Everything: Use the built in rotation features of your cloud provider (like AWS KMS annual automatic rotation) or key management service. Manual rotation is a recipe for mistakes and downtime.
- Plan Rotation Schedules: Establish a clear policy. An annual rotation is a good baseline for most data. For compliance mandates like HIPAA or PCI DSS, or for highly sensitive data, a quarterly or even monthly schedule may be necessary.
- Implement Gradual Migration: Never switch keys instantly. Maintain access to old keys for decryption while using the new key for all new encryption operations. This ensures data encrypted with older keys remains accessible until it is re encrypted over time.
- Monitor and Alert: Set up monitoring to confirm that rotation events succeed. Create alerts for any failures in the automated process, so your team can intervene immediately.
9. Secure Certificate and Key Storage
Storing your application's secret keys in a configuration file or, even worse, directly in your source code is the digital equivalent of leaving your house key under the doormat. If the application code is ever compromised or leaked, your entire security posture collapses instantly. Properly isolating cryptographic keys is one of the most fundamental data encryption best practices, ensuring that even if an attacker breaches your application layer, the crown jewels remain protected.
What Makes Storage "Secure"?
Secure key storage means physically and logically separating keys from the applications that use them. This is achieved using specialized hardware and services designed for one purpose: safeguarding cryptographic material. The goal is to make direct access to the raw key material nearly impossible. Instead of your application handling the key, it makes a request to a trusted service, which performs the cryptographic operation (like encrypting or decrypting data) on its behalf and returns the result.
The industry standards for this are Hardware Security Modules (HSMs) and cloud based Key Management Systems (KMS). An HSM is a dedicated physical appliance that generates, stores, and manages keys within a tamper resistant hardware boundary. Services like AWS CloudHSM, Azure Key Vault, and Google Cloud HSM provide this functionality as a managed cloud service, offering high availability and scalability without the need to manage physical hardware.
Actionable Tips for Implementation
To properly implement secure key storage, follow these critical guidelines:
- Never Hardcode Secrets: Your first rule is to never store keys, certificates, or any credentials in source code, configuration files, or environment variables. A compromised Git repository should never lead to a full scale data breach.
- Use a Dedicated Key Management Service: Leverage cloud provider services like AWS KMS or Azure Key Vault. They provide robust APIs, integrated IAM controls, and audit trails for all key usage, simplifying management and compliance.
- Implement Key Wrapping: For an extra layer of defense, use key wrapping. This involves encrypting your data encryption keys (DEKs) with a master key (often called a Customer Master Key or CMK) stored in an HSM or KMS. This is the core principle behind envelope encryption.
- Separate Keys by Environment: Use entirely different keys for your development, staging, and production environments. This prevents a lower environment compromise from impacting your production data.
10. Maintain Encryption Security Through Regular Audits and Testing
Implementing strong encryption is a critical first step, but it is not a "set it and forget it" solution. Think of your encryption infrastructure as a high performance engine; it requires regular tune ups and inspections to ensure it runs securely and efficiently over time. This is where regular audits and testing come in, representing one of the most vital data encryption best practices for long term security posture.
What Makes an Audit "Effective"?
An effective audit goes beyond a simple checklist. It is a comprehensive review designed to uncover vulnerabilities before attackers do. This process involves verifying everything from algorithm selection and key management procedures to implementation code and configuration settings. Companies like Apple and Google conduct relentless internal cryptographic reviews and continuous security monitoring to stay ahead of threats. Similarly, financial institutions are often mandated by regulations like PCI DSS to perform annual encryption audits.
These practices are formalized in frameworks like the NIST Cybersecurity Framework and guidelines from OWASP, which treat verification as a core security function. The goal is to create a feedback loop where you continuously test your defenses, identify weaknesses, and remediate them, ensuring your encryption remains resilient against evolving threats and implementation drift.
Actionable Tips for Implementation
To build a robust audit and testing cycle, integrate these practices into your security program:
- Schedule Audits Annually (At Minimum): Conduct comprehensive security audits of your entire encryption stack at least once a year. Engage both internal teams and specialized third party auditors for a balanced perspective.
- Implement Continuous Monitoring: Don't wait for an annual audit. Use automated tools to continuously monitor for configuration drift, anomalous access patterns in your KMS, and expiring certificates.
- Test Key Recovery and Disaster Scenarios: Regularly test your documented procedures for key recovery and disaster recovery. A backup key you cannot restore is useless.
- Leverage Security Testing Tools: Incorporate specialized application security testing tools into your development lifecycle to catch cryptographic implementation errors early.
10 Point Comparison of Data Encryption Best Practices
| Item | Implementation complexity | Resource requirements | Expected outcomes | Ideal use cases | Key advantages |
|---|---|---|---|---|---|
| Use Strong Encryption Algorithms | Medium — requires correct library selection and secure integration | Moderate CPU and vetted crypto libraries | Strong confidentiality for stored and transmitted data | Data at rest encryption, secure storage, regulatory compliance | Proven, standardized protection and wide interoperability |
| Implement Proper Key Management | High — policy, tooling, and process integration needed | HSMs/KMS, automation, specialized personnel | Reduced risk from key compromise and clear audit trails | Enterprise environments, cloud services, regulated industries | Limits exposure, centralizes control, supports compliance |
| Enable End to End Encryption (E2EE) | Very High — client side crypto and UX challenges | Client compute, secure key exchange, verification tooling | Maximum privacy; intermediaries cannot access plaintext | Private messaging, confidential communications, zero knowledge apps | Strong user privacy and protection against provider breaches |
| Use Authenticated Encryption Modes | Medium — requires nonce and AAD handling | Up to date crypto libs, modest CPU overhead | Confidentiality plus integrity and tamper detection | Network protocols, storage encryption, APIs | Prevents forgery and tampering with efficient single step ops |
| Encrypt Data at Rest, in Transit, and in Use | Very High — cross system design and integration effort | Broad infrastructure changes, HSMs, secure enclaves, compute | Comprehensive protection across data lifecycle | Cloud platforms, healthcare, finance, sensitive processing | Eliminates gaps, reduces breach impact, meets strict compliance |
| Implement Perfect Forward Secrecy (PFS) | Medium — protocol configuration and key exchange logic | CPU for ephemeral keys, updated TLS/crypto stacks | Historical session confidentiality if long term keys leak | Messaging, TLS secured services, VPNs | Limits retroactive decryption from key compromise |
| Use Secure Transport Protocols (TLS 1.3+) | Low–Medium — config and certificate management | Certificates, PKI, modern server/client stacks | Secure, performant network communications with PFS | Web services, APIs, client server apps | Modern security defaults, faster handshakes, mitigates legacy flaws |
| Implement Regular Key Rotation and Updates | High — operational processes and automation required | Automation tools, testing, coordination across systems | Reduced exposure window and patched vulnerabilities | Enterprise key lifecycles, cloud services, compliance regimes | Limits damage from compromised keys and addresses crypto aging |
| Secure Certificate and Key Storage | Medium–High — integration with secure storage services | HSMs/KMS, secure enclaves, physical security controls | Isolated keys with controlled access and auditability | Critical infrastructure, payment systems, enterprise apps | Protects against code level attacks and insider threats |
| Maintain Encryption Security Through Regular Audits and Testing | High — ongoing assessment and remediation workflows | Third party auditors, pentesters, tooling and staff time | Continuous validation of crypto posture and compliance | Regulated industries, large deployments, security focused orgs | Identifies implementation flaws and ensures standards adherence |
Your Action Plan for Better Encryption
We have traveled a long and winding road through the landscape of data encryption best practices. From the foundational choices of strong algorithms like AES 256 GCM to the architectural complexities of key management with Cloud KMS and HSMs, the journey can feel intimidating. I remember the first time I tried to implement envelope encryption in a Django project; the conceptual elegance seemed miles away from the practical snags of managing permissions and latency. The key is to see this not as a mountain to be conquered in one go, but as a series of strategic ascents.
The most critical takeaway is that encryption is not a feature you simply "add" and forget. It is a living, breathing part of your system's architecture that demands continuous care and attention. Think of it like a garden. You do not just plant the seeds and walk away; you must weed, water, and adapt to the changing seasons. Similarly, your encryption strategy requires regular key rotation, security audits, and updates to stay ahead of emerging threats and evolving compliance standards like GDPR or HIPAA.
Distilling the Essentials: Your First Steps
If you are feeling overwhelmed, let us distill this down to an actionable starting point. Your immediate goal is not to implement all ten practices overnight but to identify and plug the most significant gaps in your current setup. Start here:
- Audit Your Transport Layer: The simplest yet most impactful first step is ensuring all your services communicate over TLS 1.3. This is a non negotiable baseline. Check your load balancers, APIs, and client facing applications. It is a quick win that closes a massive potential vulnerability.
- Scrutinize Key Storage: Where are your secrets? If the answer is "in a .env file in the git repo" or "hardcoded in our Django
settings.py," that is your top priority. Migrating secrets to a dedicated manager like AWS Secrets Manager or HashiCorp Vault, and application keys to a KMS, is a transformative step for your security posture. This single change dramatically reduces your blast radius in case of a code leak. - Focus on Sensitive Data First: You do not need to encrypt every single field in your database from day one. Apply the principle of field level encryption to the most sensitive data first: personally identifiable information (PII), financial records, health information, or proprietary business logic in your RAG system's vector database. This targeted approach provides the highest security ROI for your effort.
The Bigger Picture: Why This Discipline Matters
Mastering these data encryption best practices is about more than just checking a box for a compliance audit. It is about building trust. For a startup or scale up, trust is your most valuable currency. It is the foundation upon which you build relationships with your users, attract investors, and scale your business. A single, well publicized data breach can erode that trust in an instant, setting you back years.
By embedding these principles into your engineering culture, you are not just building secure software; you are building a resilient and trustworthy organization. You are demonstrating a commitment to protecting your users' data that becomes a powerful competitive differentiator. This proactive stance on security shifts your team's mindset from a reactive, "what if we get breached?" mentality to a confident, "we are prepared" posture. This is the hallmark of a mature, production grade engineering organization. So, pick one area, start small, and build momentum. The secure, scalable system you envision is built one encrypted field and one rotated key at a time.
Feeling the weight of implementing a robust, scalable security architecture for your startup? If you are navigating the complexities of Django, Python, and GenAI systems and need a strategic partner to audit your code, design your infrastructure, or act as a fractional CTO, let's connect. As Kuldeep Pisda, I specialize in helping founders and engineering leaders build secure, production ready systems from the ground up. You can learn more about my approach at Kuldeep Pisda.
Become a subscriber receive the latest updates in your inbox.




Member discussion