It started with a weird log entry. A seemingly harmless error that, after hours of digging, turned out to be a potential security hole. It was a wake up call. As developers, we are focused on shipping features, but what happens when the pressure to deliver creates blind spots? This is not just a story about a bug; it is about realizing that our CI/CD pipelines needed a better gatekeeper. We had a problem, and the solution required a systematic way to catch these issues before they reached production, turning a manual, reactive process into an automated, proactive one.
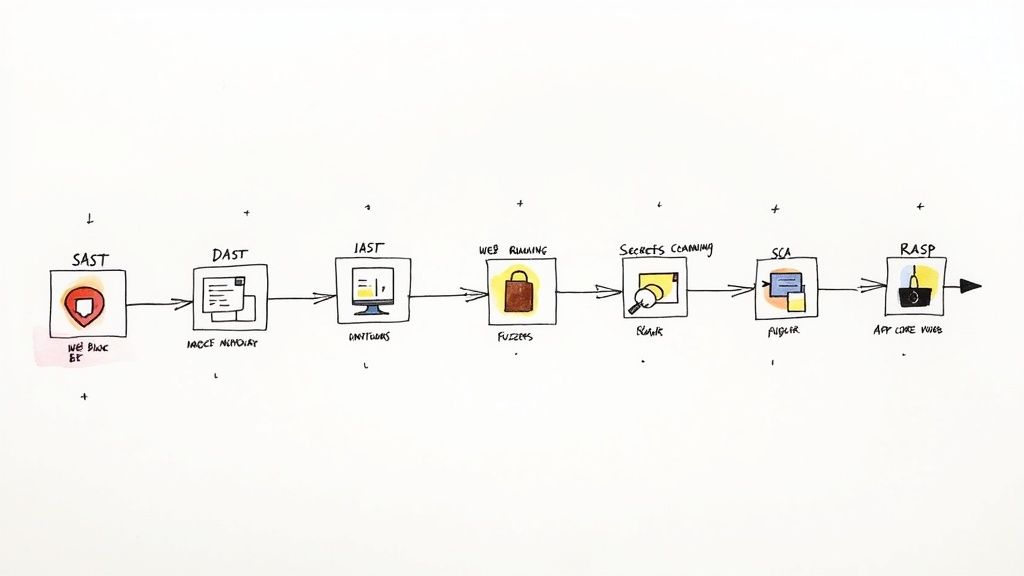
This realization sent me down the rabbit hole of application security testing tools, a world filled with acronyms like SAST, DAST, IAST, and SCA. It is easy to get lost in feature lists and marketing hype, unsure which tool actually solves your specific problem, especially within a Django or AI driven startup environment. My goal here is to give you a map based on my journey through this complex space, showing you the options I explored and where I landed.
This comprehensive guide is built to help you make informed decisions quickly. We will move beyond generic descriptions and explore the practical trade offs between open source and commercial options, integration nuances for CI/CD pipelines, and which tools are best suited for different company stages, from lean startup to scaling enterprise. Each option includes direct links and analysis to accelerate your evaluation. Let us focus specifically on how these platforms fit into a developer first workflow, helping you embed security without slowing down innovation. For those looking to delve deeper into broader cybersecurity topics and solutions, there are great resources available that cover the wider context. This article, however, stays laser focused on the tools you can implement today to secure your code.
1. PortSwigger – Burp Suite Professional / Burp Suite DAST
Burp Suite is less a single tool and more of a complete ecosystem for web application security testing. For anyone serious about manual penetration testing or deep diving into application behavior, Burp Suite Professional is the undisputed industry standard. It acts as an intercepting proxy, sitting between your browser and the target application, allowing you to inspect, modify, and replay traffic in real time. I once got stuck for hours trying to uncover a business logic flaw that automated scanners kept missing; Burp's hands on control was the only thing that let me find it.
For teams needing to scale their security efforts, PortSwigger offers a separate, automated DAST solution (formerly Burp Suite Enterprise) that integrates into the CI/CD pipeline. This allows you to schedule recurring, automated scans against your applications, providing a baseline of security coverage and flagging common vulnerabilities like SQL injection or cross site scripting without manual intervention. The real power comes from using both: automated scans for broad coverage and the professional toolkit for targeted, expert analysis.
Use Case & Implementation
- Best For: Security professionals, penetration testers, and development teams needing a powerful manual testing toolkit combined with scalable, automated DAST capabilities.
- Pricing: Burp Suite Professional is priced per user per year with a transparent self serve checkout. The automated DAST scanner is quote based, depending on the number of applications and scan agents required.
- Limitations: The per user licensing for the Professional version can become costly for larger teams. The automated scanner, while powerful, requires proper tuning to reduce false positives and effectively integrate into a fast paced development workflow.
2. ZAP by Checkmarx (OWASP ZAP)
For teams seeking a powerful, no cost entry point into dynamic application security testing, OWASP ZAP (Zed Attack Proxy) is the de facto open source standard. Now maintained under the "ZAP by Checkmarx" banner but still fully community driven and Apache 2.0 licensed, it offers a remarkable set of features for free. Like its commercial counterparts, ZAP functions as an intercepting proxy, allowing you to manually inspect and manipulate traffic, but it truly shines in its automation capabilities. It is one of the most popular application security testing tools for those on a budget or deeply invested in the open source ecosystem.
ZAP provides both automated scanning to quickly find common vulnerabilities and manual tools for deeper inspection. Its robust API and scripting support make it a favorite for CI/CD integration, allowing development teams to embed security scans directly into their build and deploy pipelines. With a huge library of add ons and a vibrant community, the platform is highly extensible, enabling you to tailor it to specific testing needs, from API security to authenticated scanning scenarios. This combination of flexibility, automation, and zero cost makes it an invaluable asset for startups and established security programs alike.
Use Case & Implementation
- Best For: Developers, QA teams, and security professionals looking for a free, highly scriptable, and community supported DAST tool to integrate into CI/CD pipelines.
- Pricing: Completely free and open source (FOSS) under the Apache 2.0 license.
- Limitations: While powerful, achieving enterprise grade reporting and vulnerability management often requires integration with other platforms or significant custom tooling. It can also produce more noise (false positives) than commercial scanners without careful tuning and context configuration.
3. Invicti (Acunetix lineage)
Invicti represents the evolution and combination of two long standing names in the DAST space, Acunetix and Netsparker. This history translates into a mature, enterprise ready platform focused on providing broad and accurate automated scanning. It stands out by combining its powerful DAST engine with optional Interactive Application Security Testing (IAST) agents. This dual approach allows the scanner to confirm vulnerabilities with a much higher degree of certainty, significantly reducing the time teams spend chasing down false positives and validating findings.
For organizations managing a large portfolio of web applications, Invicti's flexible deployment models, from SaaS to fully on premises, provide essential adaptability. Its unlimited scanning model on certain plans is a key differentiator, removing the friction of per scan or per app pricing that can discourage frequent testing. The platform is designed to be a central hub for web vulnerability management, integrating deeply with CI/CD pipelines and issue trackers like Jira, making it one of the more comprehensive application security testing tools for established security programs.
Use Case & Implementation
- Best For: Medium to large enterprises that need a scalable, integrated DAST solution with high accuracy and flexible deployment options to cover a wide range of web applications.
- Pricing: Pricing is quote based and tailored to the number of target websites and required features. It is generally geared towards enterprise budgets rather than individual users.
- Limitations: The quote based pricing model lacks transparency for smaller teams evaluating options. The feature set can be complex, and realizing its full value often requires a dedicated security team to manage and integrate the tool effectively across a large application landscape.
4. Rapid7 – InsightAppSec
Rapid7's InsightAppSec is a cloud based DAST solution designed to make comprehensive web application and API scanning accessible and straightforward. It lowers the barrier to entry for teams that need powerful, automated security testing without a steep learning curve or complex on premises setup. The platform is particularly effective for modern, complex applications, featuring a "Universal Translator" that helps it understand and test applications built on single page application (SPA) frameworks like React or Angular, which can often confuse less advanced scanners.
One of its standout features is "Attack Replay," which gives developers a direct, repeatable way to validate and understand a reported vulnerability. Instead of just getting a static report, developers can re run the exact attack payload to see the flaw in action, dramatically speeding up remediation. This focus on developer enablement, combined with strong reporting and CI/CD integrations, makes InsightAppSec a solid choice among application security testing tools for teams looking to embed security into their development lifecycle without friction.
Use Case & Implementation
- Best For: Development and security teams needing an easy to use, cloud native DAST solution that integrates well into the SDLC and provides clear, actionable results for developers.
- Pricing: Offers a transparent entry level plan billed annually, which is great for smaller teams. More advanced features and larger application counts are available in higher tier, quote based plans. It is also available via the AWS Marketplace for easier procurement.
- Limitations: The annual billing model requires some upfront budget planning. While the entry tier is accessible, scaling up to unlock the most advanced capabilities will require moving to a higher cost plan.
5. Qualys – Web Application Scanning (WAS) / TotalAppSec
Qualys takes a platform first approach to security, and its Web Application Scanning (WAS) module is a core component of that ecosystem. Designed for enterprises managing vast and complex application portfolios, Qualys provides a powerful, cloud based DAST solution that excels at scale. It automates the discovery, cataloging, and scanning of web applications and APIs, offering a centralized command center for security teams overseeing hundreds or even thousands of digital assets. This makes it one of the go to application security testing tools for organizations needing broad, consistent coverage.
The platform's strength lies in its unification. The TotalAppSec offering combines DAST with API scanning, providing a holistic view of an application's attack surface, a critical capability as modern architectures become more interconnected. For more information on securing these crucial endpoints, check out this guide to REST API design principles. Integrations with CI/CD tools like Jenkins and ITSM platforms like ServiceNow allow findings to flow directly into existing developer and operational workflows, streamlining remediation efforts across large, distributed teams. The robust reporting and dashboarding capabilities are built for executive oversight and compliance tracking.
Use Case & Implementation
- Best For: Large enterprises and security teams needing a scalable, centralized DAST and API security platform to manage a large inventory of web applications.
- Pricing: Pricing is quote based and depends on the number of web applications, modules selected, and desired scan frequency. It is geared towards enterprise budgets.
- Limitations: The sheer breadth of the Qualys platform can present a significant learning curve for new users. The pricing model is less suited for small teams or startups with only a handful of applications to secure.
6. Veracode – Application Risk Management Platform
Veracode presents a comprehensive, enterprise grade SaaS platform designed to manage application risk from code to cloud. It moves beyond a single tool, offering a unified solution that integrates Static Analysis (SAST), Dynamic Analysis (DAST), and Software Composition Analysis (SCA) into the software development lifecycle (SDLC). This approach is particularly effective for large organizations aiming to standardize their security posture and provide developers with consistent, actionable feedback directly within their existing workflows, like IDEs and CI/CD pipelines.
What sets Veracode apart is its developer centric focus and the use of AI to streamline remediation. Instead of just flagging vulnerabilities, the platform provides AI powered advice and suggests the "next best action" for developers to take, reducing the time spent on fixing security issues. This focus on education and efficient fixes helps mature a development team's security practices over time. The platform's extensive support for over 100 languages and various application types makes it a versatile choice for organizations with diverse technology stacks. For more on securing application data, consider these best practices for storing passwords securely.
Use Case & Implementation
- Best For: Enterprises and large organizations seeking a unified, scalable AppSec platform that integrates multiple testing types and provides strong developer support and SDLC integration.
- Pricing: Pricing is quote based and tailored to the organization's needs, depending on the specific modules (SAST, DAST, SCA) and the scope of applications being scanned. It is not publicly available.
- Limitations: The sales led pricing model can be a hurdle for smaller teams or startups looking for transparent, self service options. The platform's comprehensive nature may also represent a significant investment and require dedicated effort to fully integrate and manage.
7. Checkmarx One – Unified AppSec
For enterprises looking to consolidate their security tooling and manage risk from a single vantage point, Checkmarx One presents a comprehensive, unified platform. It moves beyond single point solutions by integrating SAST, DAST, SCA, API Security, and Infrastructure as Code (IaC) scanning into one cohesive ecosystem. This approach is designed to break down silos between different security functions, providing a centralized view of application risk that helps teams prioritize remediation efforts more effectively based on correlated findings.
The platform is built for enterprise scale, offering extensive language coverage, deep CI/CD integrations, and robust role based access controls. A key advantage for organizations heavily invested in cloud infrastructure is its availability in the AWS Marketplace, which can simplify procurement and billing. By combining multiple application security testing tools under one roof, Checkmarx helps reduce the friction and toolchain fragmentation that often plague large development environments, allowing security and development teams to work from a shared source of truth.
Use Case & Implementation
- Best For: Large enterprises and security teams seeking a consolidated AppSec platform to replace multiple disparate tools and manage risk across a complex application portfolio.
- Pricing: Pricing is quote based and tailored to enterprise needs, reflecting the platform's comprehensive nature. Some modules are available for purchase directly through the AWS Marketplace, which can offer more transparent pricing tiers.
- Limitations: The platform's extensive capabilities and enterprise focus mean it can be cost prohibitive for small teams or startups. The complexity of a unified system also requires a dedicated effort for initial setup and configuration to maximize its value.
8. Synopsys – Polaris Software Integrity Platform
Synopsys brings its long standing enterprise security expertise to the cloud with the Polaris Software Integrity Platform. This is not just one tool; it's a unified SaaS platform designed to centralize and automate security across the entire development lifecycle. By integrating its powerful SAST, SCA (rooted in its Black Duck heritage), and DAST scanning engines into a single dashboard, Polaris aims to give large organizations a comprehensive view of their application risk without the friction of managing disparate tools.
The platform is built for modern DevSecOps workflows, emphasizing automation and scalability. A key differentiator is Polaris Assist, its AI powered assistant that provides vulnerability summaries and actionable code fix suggestions directly within the workflow. This helps development teams remediate issues faster and reduces the burden on security teams. For organizations looking for a single vendor to provide a full suite of enterprise grade application security testing tools, Polaris presents a compelling, integrated solution.
Use Case & Implementation
- Best For: Large enterprises and regulated industries seeking a unified, scalable platform for SAST, SCA, and DAST that integrates deeply into automated CI/CD pipelines.
- Pricing: Pricing is quote based and tailored to enterprise needs, typically depending on the number of developers, applications, and modules (SAST, SCA, DAST) required.
- Limitations: The platform is an enterprise first solution, which may make it less accessible or cost effective for smaller teams. The full value is best realized when adopting the entire suite of tools together, which represents a significant commitment.
Visit Website
9. HCL AppScan on Cloud – Marketplace (pay per scan)
HCL AppScan has been a long standing player in the enterprise application security testing tools space, but its traditional procurement model was often a hurdle for smaller teams or projects with variable needs. The AppScan on Cloud Marketplace directly addresses this by offering a pay per scan model. This provides a low friction path for teams to purchase a specific number of SAST, DAST, or SCA scans using a simple credit card checkout, bypassing lengthy enterprise sales cycles. This is a significant shift, making powerful scanning technology accessible for ad hoc projects or compliance requirements.
Each purchase on the marketplace grants a one year SaaS subscription to the AppScan on Cloud platform, where you can manage your scan targets, run tests, and review findings. The platform provides centralized dashboards, policy management, and actionable reports with remediation guidance to help developers fix identified vulnerabilities. This model is ideal for organizations that do not need a continuous, high volume scanning program but require professional grade tools for periodic assessments or to satisfy a specific security audit. It effectively unbundles enterprise capabilities for metered consumption.
Use Case & Implementation
- Best For: Startups, SMBs, or individual project teams needing occasional, high quality SAST/DAST/SCA scans without committing to a large annual subscription.
- Pricing: Transparent, public pricing per scan is available on the marketplace website. Scans are purchased in packs with a minimum transaction of five scans.
- Limitations: The purchased scans expire after one year, which might not be cost effective for teams with consistent, ongoing scanning needs. The five scan minimum purchase could be a barrier for a one off project, and larger organizations will likely find the traditional subscription model more economical for continuous security programs.
10. Snyk – Developer first AppSec
Snyk has carved out a significant niche by building an entire application security testing platform with a developer first mindset. Where many tools are built for security teams and then adapted for developers, Snyk starts in the IDE and the pull request. It integrates directly into the developer workflow, offering automated scanning for open source dependencies (SCA), code vulnerabilities (SAST), container images, and even Infrastructure as Code (IaC) configurations. This tight integration provides immediate feedback where developers are already working.
The platform's standout feature is its focus on remediation. Instead of just flagging a vulnerable package, Snyk often suggests the minimal version upgrade needed to resolve the issue and can even generate an automated pull request to apply the fix. This drastically reduces the friction between identifying and fixing security debt. While its core strengths are in SCA and SAST, Snyk also offers DAST and API security testing as add ons, allowing teams to consolidate their AppSec program onto a single, developer friendly platform. It's a powerful approach that shifts security left by empowering developers to own their code's security posture.
Use Case & Implementation
- Best For: Development teams looking for a highly integrated, developer friendly platform to manage SAST, SCA, and container security directly within their existing workflows.
- Pricing: Offers a generous free tier for individual developers. Paid plans are based on the number of "contributing developers," with specific costs for Team and Business plans requiring sign in or a sales conversation. Enterprise features are quote based.
- Limitations: The DAST and API testing capabilities are add on products and not as central to the platform's core offering as its code and dependency scanning. The "per contributing developer" pricing model can become complex and costly for large organizations with many contributors.
11. AWS Marketplace – Application Security (AST) Category
For teams deeply embedded in the AWS ecosystem, procuring software through the AWS Marketplace can dramatically simplify accounting and vendor management. Instead of being a single tool, this is a centralized hub where you can find, try, and buy a wide range of commercial application security testing tools from leading vendors like Checkmarx, Invicti, and Rapid7. This approach streamlines the entire procurement process, allowing you to leverage your existing AWS account for billing and potentially count purchases towards your AWS Enterprise Discount Program (EDP) commitment.
The primary advantage is consolidation. Rather than juggling multiple contracts and payment portals, everything is handled through your AWS bill. This is especially useful for startups and scale ups looking to minimize administrative overhead. The marketplace facilitates side by side comparisons, often with free trials and various deployment options available directly from the listing. For larger organizations, the ability to negotiate private offers through the marketplace provides a familiar and efficient procurement workflow. While it simplifies purchasing, remember that you are still acquiring individual tools, each with its own learning curve and integration requirements, including the need for robust API security. For a deeper look into securing your APIs, explore these API documentation best practices.
Use Case & Implementation
- Best For: Organizations already committed to the AWS cloud that want to simplify procurement, consolidate billing, and manage software licenses for various AST tools through a single vendor relationship.
- Pricing: Varies widely by vendor. Some listings have public pricing tables for different tiers, while others are quote based or require engaging with the vendor for a private offer.
- Limitations: Not all security tools or their specific SKUs are available. Some listings still require direct sales engagement, slightly diminishing the "self serve" benefit. You are limited to the vendors who have chosen to list their products on the platform.
12. G2 – AppSec Software Category Pages
While not a testing tool itself, G2 is an indispensable resource for navigating the crowded market of application security testing tools. It functions as a peer review and comparison platform, offering dedicated, live category pages for SAST, DAST, IAST, and more. This makes it an excellent starting point for creating a vendor shortlist, understanding market sentiment, and quickly comparing the advertised features of various commercial solutions before you even start a sales conversation.

The real value of G2 lies in its aggregated user reviews and grid reports, which provide a high level view of market leaders, contenders, and niche players. You can filter by company size, user satisfaction, and specific features to narrow down options relevant to your needs. This process helps cut through marketing noise, offering insights from actual users about usability, support quality, and integration challenges, which is crucial data when evaluating how a tool will fit into your existing development workflow and culture.
Use Case & Implementation
- Best For: Engineering leaders, security managers, and procurement teams conducting market research to shortlist and compare commercial AST vendors.
- Pricing: Free to access all reviews and comparison data. Vendors pay G2 for enhanced profiles and lead generation features, but the core data is available at no cost to the user.
- Limitations: Reviews can sometimes be influenced by vendor campaigns, so it is important to read a wide sample. Enterprise pricing is almost never listed, and some product descriptions are vendor supplied, requiring further due diligence on your part.
Top 12 AppSec Testing Tools Comparison
| Product | Core features | Target audience | Key strengths | Pricing & procurement |
|---|---|---|---|---|
| PortSwigger – Burp Suite Professional / DAST | Intercepting proxy, manual tools (Repeater/Intruder), automated DAST & reporting | Pentesters, security teams needing hands on testing + scheduled scans | De facto industry standard, rich extensions ecosystem, strong docs | Professional: per user license (self serve); DAST/Enterprise: quote based |
| ZAP by Checkmarx (OWASP ZAP) | Automated & manual scans, proxy, CI/CD scripting, auth recorders | Devs, QA, small security teams seeking no cost scanner | Open source (Apache 2.0), free, extensible, good CI support | Free to use; commercial integrations/enterprise features optional |
| Invicti (Acunetix lineage) | DAST + optional IAST, CI/CD & ticketing integrations, cloud/on prem options | Enterprises needing enterprise scanning with low false positives | Flexible deployment (cloud/on prem/air gap), broad integrations | Quote based; licensing models vary (some offer unlimited scan plans) |
| Rapid7 – InsightAppSec | Click to scan, Attack Replay, 95+ attack types, reporting & integrations | Teams wanting cloud DAST with developer friendly workflows | Easy onboarding, transparent starter pricing, AWS Marketplace | Free trial; starter pricing published, annual billing; higher tiers quote based |
| Qualys – WAS / TotalAppSec | Automated crawling, OWASP/CWE coverage, CI/CD & central dashboards | Large enterprises with thousands of apps and centralized AppSec | Scales to very large portfolios, unified platform & reporting | Quote based, pricing depends on app counts and modules |
| Veracode – Application Risk Management | SAST, DAST, SCA, AI remediation guidance, IDE & SDLC integrations | Enterprises seeking unified code to cloud AppSec program | Mature SaaS, developer workflows, comprehensive scanning modalities | Sales led pricing (quote based); cost scales with scope/modules |
| Checkmarx One – Unified AppSec | SAST/DAST/SCA/API/IaC scanning, risk based dashboards, AI features | Large orgs aiming to consolidate AppSec toolchain | Platform consolidation, enterprise onboarding, AWS Marketplace listings | Enterprise minimums typical; pricing via quote or marketplace |
| Synopsys – Polaris Software Integrity | Unified SAST/SCA/DAST (fAST), AI assisted fix suggestions, DevSecOps automation | Enterprises automating DevSecOps and large scale scanning | Strong accuracy pedigree, automation first, enterprise support | Quote based; best value when multiple modules adopted |
| HCL AppScan on Cloud – Marketplace | Pay per scan purchases, centralized dashboards, actionable reports | Teams needing metered/occasional scans without enterprise contracts | Transparent public pricing, low friction credit card procurement | Pay per scan (min. 5 scans), one year SaaS per purchase |
| Snyk – Developer first AppSec | IDE/PR integrations, SAST/SCA/container/IaC, optional API/DAST add ons | Developers and small to mid engineering teams | Easy dev adoption, free tier, automated fix PRs | Free & team plans self serve; enterprise pricing via quote (per contributing dev) |
| AWS Marketplace – Application Security | Consolidated listings, procurement, private offers, consolidated billing | Organizations buying AST via AWS procurement channels | Streamlined contracting, side by side vendor trials, billing via AWS | Marketplace billing; some SKUs show pricing, others require vendor quotes |
| G2 – AppSec Category Pages | Vendor comparisons, user reviews, grid reports, searchable filters | Buyers shortlisting vendors and reading peer reviews | Quick sentiment checks, broad market coverage, free access | Free to browse; vendor pricing typically not shown (leads to vendor pages) |
So, What's Your Next Move?
We've just navigated the expansive and often overwhelming world of application security testing tools. From the developer friendly interface of Snyk to the all encompassing platform of Checkmarx One, the options are as varied as the vulnerabilities they aim to uncover. The journey from recognizing the need for security to implementing a robust testing strategy can feel like trying to drink from a firehose. But the core lesson is not to adopt every tool we have discussed. The real goal is to build a security culture, one tool and one process at a time.
Remember the story we started with, the late night panic over a potential data breach? The tools we have explored are your proactive defense against that very scenario. They are the guardrails that keep your development velocity high without sacrificing safety. The best set of application security testing tools for your startup is not the most expensive or the most feature rich. It is the one that integrates seamlessly into your workflow, provides actionable feedback your developers can use, and actually gets used consistently.
Charting Your Course: From Theory to Action
Feeling a bit of analysis paralysis? That is completely normal. Let's pause and break down the next steps into a practical, manageable plan. You do not need to boil the ocean; just start by heating the kettle.
- Start with the "Low Hanging Fruit": Before you even think about complex DAST or IAST implementations, look at what you can do for free, right now. Run Snyk's free tier or OWASP Dependency Check on your Django project's
requirements.txt. The insights you gain from Software Composition Analysis (SCA) are often the easiest to fix and can prevent a huge class of common vulnerabilities. It is a quick win that builds momentum. - Pick One Core Practice to Master: Choose either SAST or DAST as your primary focus for the next quarter. If your team is more comfortable in their IDEs, a SAST tool like Semgrep or the entry level plans from Veracode might be a perfect fit. If you want to test your running application as a black box, a DAST tool like OWASP ZAP or a paid scanner like Invicti against a staging environment is your best bet. Do not try to do everything at once.
- Integrate, Do not Just Scan: The true power of modern application security testing tools is unlocked when they become part of your CI/CD pipeline. A scan that runs manually once a month is a report; a scan that runs on every pull request is a process. This shift from periodic auditing to continuous assurance is the most critical step you can take. Automating a secrets scanner like GitGuardian or TruffleHog is another foundational step that prevents catastrophic, yet simple, mistakes.
Beyond the Tool: The Human Element
Ultimately, these tools are instruments in the hands of your developers, security champions, and operations teams. Fostering a blameless security culture is paramount. When a tool flags a vulnerability, it should be seen not as a developer's mistake but as a system weakness that everyone can learn from. Use the findings to educate the team, improve coding standards, and refine your security policies. This human layer is what transforms a set of disparate tools into a cohesive security program.
Remember, application security is not a destination but an ongoing journey of improvement. The landscape of threats and defenses is constantly evolving. A tool that is perfect for you today might need to be augmented or replaced tomorrow as your company scales and your architecture matures. The key is to remain curious, agile, and committed to the process. As you build out your security stack, it's also wise to understand how these tools fit into the bigger picture of managing business risk. To understand how application security fits into a wider strategy, consider exploring comprehensive software risk solutions that encompass not just code, but people, processes, and third party dependencies. Your first step today, no matter how small, is a deposit into your company's future resilience.
As a consultant, I specialize in helping startups and scale ups, particularly those building with Django and AI, navigate these exact challenges. If you are architecting a secure development lifecycle or need an experienced hand to guide your security strategy, I am here to help. You can learn more about my work and how we can collaborate at Kuldeep Pisda.
Become a subscriber receive the latest updates in your inbox.


Member discussion