Let's be honest. Setting up Django REST Framework authentication can feel like assembling IKEA furniture in the dark. You know all the pieces are there—sessions, tokens, JWTs—but the instructions seem written in another language, and you have this nagging fear that one wrong move will leave your API wide open.
I have been there. I once got stuck on a bug for hours before realizing my frontend was sending the Authorization header with a lowercase "a". It's the kind of thing that makes you question your life choices.
That initial struggle is a rite of passage. It means you are already thinking beyond just "does it work?" and asking "is it secure?" Robust authentication is not a feature; it is the foundation of a trustworthy API. While Django's built in tools are fantastic for traditional web apps, they lean heavily on sessions and cookies. That is great for a monolith, but it just does not play well with modern single page applications or mobile clients that speak stateless languages.
This is exactly where DRF shines. It gives us the flexible, powerful tools needed to lock down these modern interactions. It is no surprise that as Django's popularity grows, so does the reliance on DRF for building secure backends. A 2023 JetBrains survey found that about 64% of developers use Django for work or personal projects, and a huge slice of them are definitely building APIs.
So, let us journey together from that initial "I think this is secure?" feeling to "I know exactly how this works and why I chose this path." We are going to explore the options, weigh the tradeoffs, and build something solid.
Why Your API Security Strategy Is More Than Just a Password Field
An API without proper authentication is a liability waiting to happen. It is not just about who can see the data, but who can change it. Unsecured endpoints are an open invitation for data breaches, unauthorized modifications, and a complete loss of user trust. Think of authentication as the bouncer at your club; it decides who gets in.
Without it, you can't properly handle:
- Protecting User Data: Your first and most critical responsibility.
- Preventing Abuse: Rate limiting and access control stop bad actors from overwhelming your service.
- Enabling Tiered Access: Different users (e.g., free vs. premium, user vs. admin) require different permissions.
A strong authentication setup is just one piece of the puzzle. It is essential to understand comprehensive API security best practices to fully protect your application. This includes not just authenticating users, but also properly handling their credentials. We have got a whole guide on how to store password securely in the database that dives deep into that crucial topic.
This guide will walk you through the essential strategies for implementing production grade security, helping you build APIs that are not just functional but fundamentally secure.
Comparing Your DRF Authentication Options: The Great Buffet of Choices
Diving into the Django REST Framework documentation can feel overwhelming. Session, Basic, Token, JWT—where do you even start? It's a common paralysis point for developers, and I have certainly spent my fair share of time weighing the options on new projects.
This decision is more than just a technical detail; it sets the foundation for how your frontend will interact with your API. Let's break down the main contenders in a way that connects to real world project needs, moving beyond just the specs to the actual developer experience.
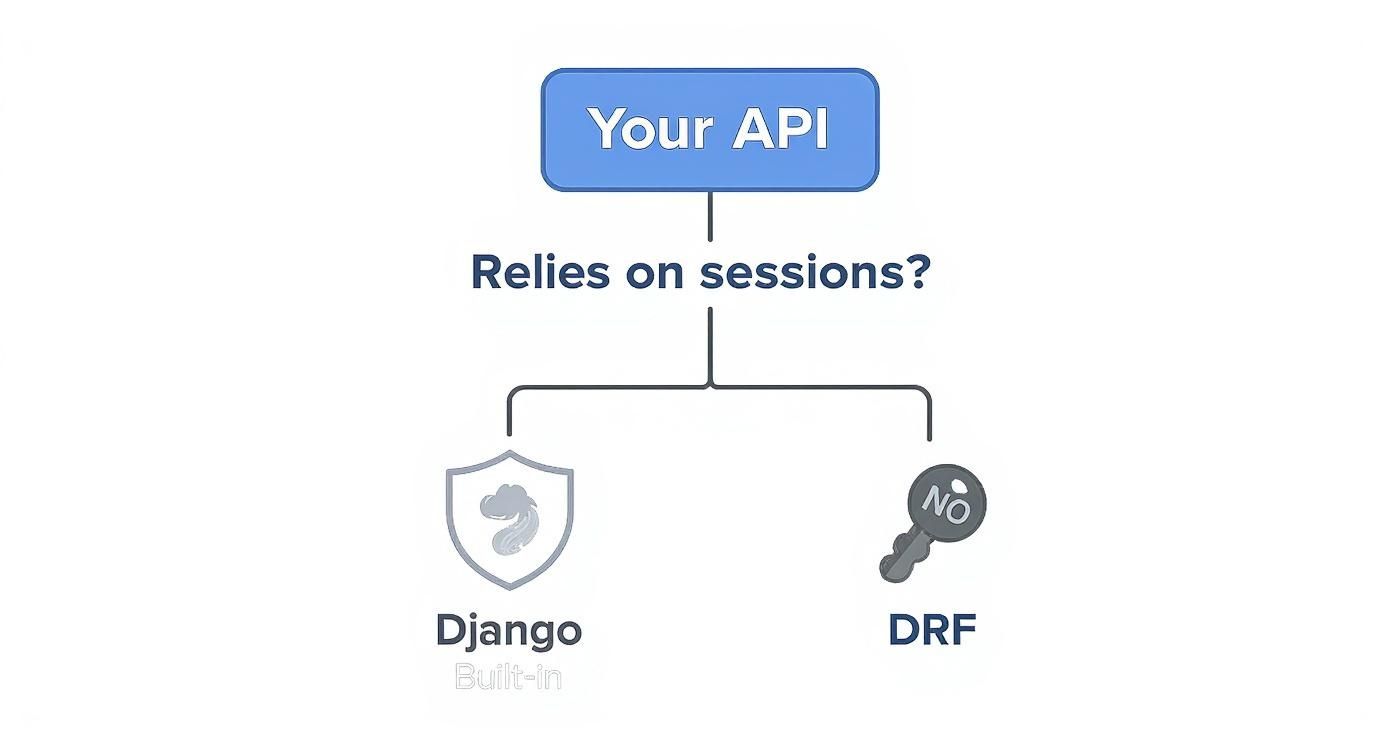
When your API needs something more than what traditional Django offers.
The key takeaway here is that if your API is tightly coupled with a traditional Django frontend, sticking with sessions is often the simplest path. For everything else, especially decoupled frontends or mobile apps, DRF provides the specialized tools you need.
To make this choice a little easier, I have put together a quick comparison table that summarizes the key differences at a glance. Think of it as a cheat sheet for picking the right tool for the job.
DRF Authentication Methods Compared
| Method | Statefulness | Best For | Key Tradeoff |
|---|---|---|---|
| Session Auth | Stateful | Traditional Django web apps with integrated frontends. | Does not work well with mobile apps or SPAs due to cookie reliance. |
| Token Auth | Stateless | SPAs, mobile apps, and server to server communication. | Requires a database lookup on every single request to validate the token. |
| JWT | Stateless | High performance, scalable APIs, and microservices. | More complex to manage token expiration, refresh logic, and security. |
Each of these has its place, and knowing when to use which one is a hallmark of an experienced Django developer. Let's dig into the details a bit more.
SessionAuthentication: The Familiar Choice
If you're coming from a standard Django background, SessionAuthentication is your old friend. It leans on Django's built in session backend, which means it uses cookies to handle state. This is fantastic for traditional web applications where your frontend and backend live on the same domain.
But its reliance on cookies and stateful server side sessions makes it a poor fit for many modern use cases. Mobile applications and third party services often struggle with, or simply can't use, cookie based authentication.
SessionAuthentication is the path of least resistance for traditional web apps. But the moment you need to support a mobile client or a separate single page application, you will feel its limitations.
TokenAuthentication: The Reliable Workhorse
This is often the default choice for a good reason. TokenAuthentication is a straightforward, stateless approach where each user is issued a unique token. The client then includes this token in the Authorization header of every request. Simple and effective.
It's easy to implement, widely understood, and a solid choice for:
- Single Page Applications (SPAs): Your React or Vue frontend can easily store the token and send it with each API call.
- Mobile Apps: Native iOS and Android apps can securely store the token on the device.
- Server to Server Communication: It's a clean way for other services to authenticate with your API.
The beauty of token auth lies in its simplicity. If you want to learn more about the mechanics, our guide on how to make REST APIs in Django using Django REST Framework provides a great foundation. Its primary drawback? The token itself contains no data; it's just an identifier, requiring a database lookup every single time to verify the user.
JWT: The Powerful Newcomer
JSON Web Tokens (JWT) represent a more advanced, stateless option. Unlike simple tokens, a JWT is a self contained, digitally signed JSON object. This token can hold user information—like a user ID and roles—directly within its payload.
This means you can verify the user and their permissions without hitting the database on every request. That's a huge performance win for distributed systems or microservices. The tradeoff is increased complexity. You suddenly have to manage token expiration, refresh tokens, and the potential security risk of storing data in the token payload. Choose JWT when scalability and statelessness are your absolute top priorities.
How to Build a Secure Endpoint with Token Authentication
Alright, enough theory. Let's get our hands dirty and actually write some code. This is where we shift from abstract concepts to a concrete implementation, building a secure API endpoint from the ground up using DRF's built in TokenAuthentication.
It's surprisingly straightforward once you see how all the pieces connect.
I remember the first time I did this, I was amazed at how little boilerplate was required. Django and DRF handle so much of the heavy lifting, which lets us focus on the important stuff—our application's logic. Let's walk through the whole process together.
Setting Up the Token Backend
Before we can even think about using tokens, we need to tell Django about DRF's token authentication application. This handy little app provides the database model required to store tokens and link them to your users.
Just open up your project's settings.py file and make two quick additions.
First, you'll need to add rest_framework.authtoken to your INSTALLED_APPS list. This is how you register the token app with your project.
# settings.py
INSTALLED_APPS = [
# ... other apps
'rest_framework',
'rest_framework.authtoken', # Add this line
# ... your project's apps
]
Second, you'll want to configure DRF to use TokenAuthentication by default. This is a global setting that tells DRF to look for a token in the request headers for any view that requires authentication. It's a huge time saver.
# settings.py
REST_FRAMEWORK = {
'DEFAULT_AUTHENTICATION_CLASSES': [
'rest_framework.authentication.TokenAuthentication',
],
# While we are here, let's set a default permission policy too.
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.IsAuthenticated',
]
}
With those settings in place, the last bit of setup is to update our database schema. Since DRF's authtoken app includes a Token model, we need to create the actual table for it.
Just pop open your terminal in the project's root directory and run the migrate command:
python manage.py migrate
You should see some output confirming that the authtoken migrations were applied. And just like that, your database is ready to start storing authentication tokens.
Protecting an Endpoint
Now for the fun part. Let's create a simple view and lock it down so only authenticated users with a valid token can get in.
Imagine we have a view that's supposed to return the current user's profile data. This is classic protected information—you definitely do not want just anyone accessing it.
In your app's views.py, you can define a view like this:
# myapp/views.py
from rest_framework.views import APIView
from rest_framework.response import Response
from rest_framework.permissions import IsAuthenticated # Import this
class UserProfileView(APIView):
# This little line is the bouncer at the door
permission_classes = [IsAuthenticated]
def get(self, request):
# Because of IsAuthenticated, request.user will be a valid User instance
user_data = {
'username': request.user.username,
'email': request.user.email,
}
return Response(user_data)
See that permission_classes = [IsAuthenticated] line? That single line is doing all the work. It hooks directly into DRF's authentication and permission system.
When a request comes in, DRF first runs the authentication checks we configured (in our case, TokenAuthentication). If the token is valid, it finds the corresponding user and attaches their User object to the request.
Only then does the IsAuthenticated permission class kick in. It simply checks if request.user exists and is authenticated. If not, it immediately cuts things short and returns a 401 Unauthorized response. Your view's get method is never even called.
This separation of concerns is a core strength of the Django REST Framework. Authentication classes figure out who the user is, while permission classes decide what they are allowed to do.
Generating and Using a Token
So, how does a user actually get a token in the first place? We need to give them an endpoint for that. Thankfully, DRF has our back with a pre built view that handles it all.
Let's wire it up in your project's urls.py:
# myproject/urls.py
from django.urls import path
from rest_framework.authtoken.views import obtain_auth_token
from myapp.views import UserProfileView
urlpatterns = [
path('api/profile/', UserProfileView.as_view(), name='user_profile'),
path('api/token/', obtain_auth_token, name='api_token_auth'),
]
The obtain_auth_token view is designed to accept a POST request containing a user's username and password. If the credentials check out, it returns a JSON response with their authentication token.
A frontend application would then store this token securely and include it in the Authorization header for all future requests to protected endpoints, like our /api/profile/ view. The header needs to be formatted like this: Authorization: Token <the_actual_token>.
And that's really all there is to it. You have successfully built a secure, token protected endpoint.
Leveling Up Your API with JSON Web Tokens
Alright, so you have got Token Authentication down. That is a huge milestone. But what happens when your app starts to take off? What if you need to embed user roles directly into your tokens, or set a firm expiration date without hammering the database on every single request?
This is where the game changes. It is time to bring in JSON Web Tokens (JWT).
Think of the simple token we just built as a basic hotel key card. It opens the door, and that is about it. A JWT, on the other hand, is like a modern smart card. It does not just open the door; it holds your access level, your checkout date, and maybe even your dinner reservation. All that data is self contained and cryptographically verified.
This is our deep dive into the world of stateless django rest framework authentication. We're moving from a simple key to an intelligent credential.
Why JWTs are a Scalability Game Changer
The real magic of a JWT is in its structure. It's a self contained JSON object, digitally signed to prove it has not been tampered with. This signature is absolutely critical—it allows the server to trust the data inside the token without having to look up anything in the database.
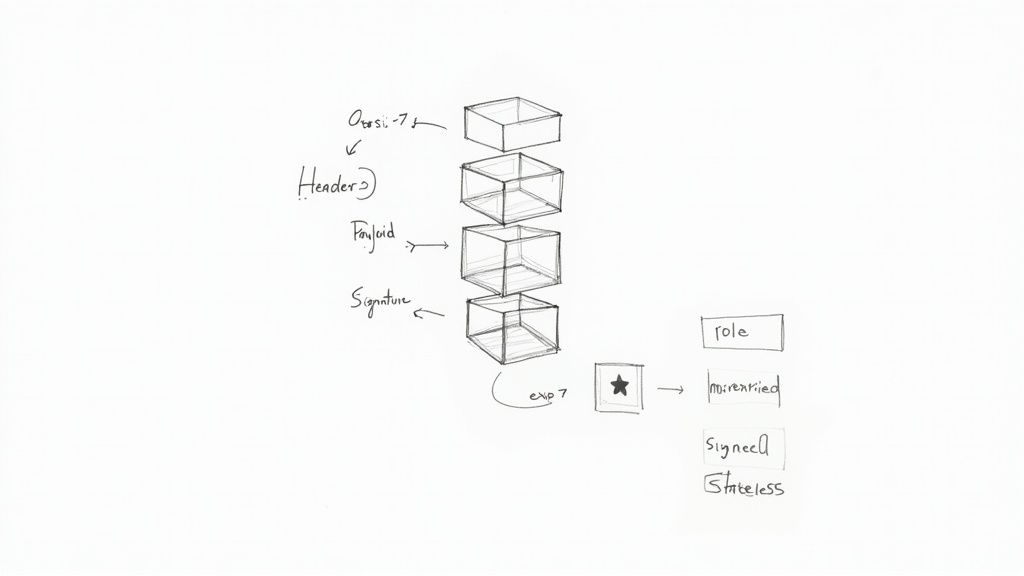
A JWT is made of three parts, separated by dots:
- Header: This contains metadata, like the signing algorithm being used (e.g., HS256).
- Payload: This is the good stuff. It holds the "claims," which are statements about an entity (usually, the user) and other handy data. You can tuck a user ID, roles, permissions, or an expiration timestamp right in here.
- Signature: A cryptographic signature created using the header, the payload, and a secret key. This is how we guarantee the token's integrity. The concepts behind this are fascinating; our guide on symmetric vs asymmetric keys explained through Hollywood magic gives a really fun and visual breakdown.
This stateless nature is a massive win for performance. It's especially powerful in a microservices architecture where you might have dozens of services that all need to know who a user is. Instead of each service hitting a central user database, they can just validate the JWT's signature and be on their way.
Getting Started with djangorestframework-simplejwt
The community has largely settled on djangorestframework-simplejwt as the go to package for this. It's well maintained and does the job beautifully. Let's get it installed and wired up.
First things first, pull it in with pip:
pip install djangorestframework-simplejwt
Next, we need to tell DRF to use its authentication classes instead of the default TokenAuthentication. Pop open your settings.py:
# settings.py
REST_FRAMEWORK = {
'DEFAULT_AUTHENTICATION_CLASSES': (
'rest_framework_simplejwt.authentication.JWTAuthentication',
)
}
Finally, we just need to expose the package's built in views for getting and refreshing tokens. Let's add them to our main urls.py.
# myproject/urls.py
from django.urls import path
from rest_framework_simplejwt.views import (
TokenObtainPairView,
TokenRefreshView,
)
urlpatterns = [
# ... other urls
path('api/token/', TokenObtainPairView.as_view(), name='token_obtain_pair'),
path('api/token/refresh/', TokenRefreshView.as_view(), name='token_refresh'),
]
With just those few steps, you have now got endpoints that provide a user with an access token (the short lived key for accessing resources) and a refresh token (the long lived key used to get a new access token).
The widespread adoption of Django directly fuels the need for robust solutions like this. Django powers a huge slice of the web; some surveys show it holds about 33.22% of the market share among Python frameworks. This popularity means libraries like simplejwt become critical tools for securing the thousands of APIs built on Django. You can discover more insights about Django's market presence on TMS Outsource.
This is how you go from securing a simple API to designing a truly scalable authentication system.
Common Authentication Pitfalls and How to Avoid Them
Building a feature is one thing; building it so it does not create a massive security hole is something else entirely. This part of the journey is about the hard won lessons from years of debugging APIs. It's the stuff I really wish someone had told me when I first started my adventure with django rest framework authentication.
Let's talk about the number one mistake I see developers make: storing tokens improperly on the client side. I once spent days tracing a bizarre bug only to realize a frontend was leaking tokens through its logging service. A painful but valuable lesson.
Never, ever store JWTs or API tokens inlocalStorage. It's a prime target for Cross Site Scripting (XSS) attacks. A malicious script injected onto your page can read everything inlocalStorageand send your users' tokens straight to an attacker.
So what should you do instead? You have got a couple of solid options:
- HTTPOnly Cookies: This is the gold standard for web clients. The cookie gets sent automatically with each request, but it's completely inaccessible to JavaScript, which shuts down XSS threats cold.
- In Memory Storage: For Single Page Applications (SPAs), you can just store the token in a JavaScript variable. This is secure against XSS because the token vanishes on a page refresh, but it does mean you need a clear strategy for re authenticating users when they revisit.
The Challenge of JWTs
While JWTs are incredibly powerful, they come with their own unique set of headaches. Authentication related issues are a huge deal, consistently ranking among the top causes of API security breaches. Industry reports show that broken authentication accounts for roughly 23% of all API vulnerabilities exploited by attackers. You can discover more insights about API security challenges on Planeks.
One of the biggest gotchas is forgetting that JWTs are stateless by design. This makes token revocation—the act of invalidating a token before it expires—surprisingly tricky.
Think about it: if a user's token is compromised, you can't just delete it from a database column like you would with a simple API token. You need a plan from day one. This usually involves maintaining a blacklist of revoked tokens that you check with every single request, which, ironically, slightly defeats the purpose of a fully stateless system. It's a tradeoff you absolutely have to make consciously.
Wrapping Up: A Final Checklist for Your DRF API Security
We have covered a lot of ground, from the fundamentals of authentication to the nitty gritty of tokens and permissions. Now, let's distill all that into a quick reference—a final checklist I run through every time I start a new project. Getting these things right from day one saves a world of pain later.
The truth is, effective django rest framework authentication is not about chasing a single "best" solution. It's about making smart, deliberate choices that actually fit what you are building. Every decision, from how you store a token to how you handle permissions, stacks on top of the last.
Your Go To Authentication Checklist
Think of these as the non negotiables. Remembering these fundamentals will prevent so many future headaches.
- Token vs. JWT: For most standard Single Page Apps (SPAs) and mobile apps,
TokenAuthenticationis your workhorse. It's simple and gets the job done. Only reach for JWTs (usingdjangorestframework-simplejwt) when you absolutely need stateless scalability, need to embed custom claims in the token itself, or you are deep in a microservices architecture. - The Golden Rule: Never Use
localStorage: Seriously, just do not. Storing any kind of token inlocalStorageis an open invitation for Cross Site Scripting (XSS) attacks. For web clients, secure HTTPOnly cookies are the way to go. For SPAs, keeping the token in memory is a much safer bet. - Permissions Are Your Best Friend: This is a big one. Authentication tells you who the user is, but permission classes (
IsAuthenticated,IsAdminUser, or your own custom ones) are what define what they are actually allowed to do. Use them everywhere to enforce your app's rules. - Have a Plan for Token Revocation: Do not treat this as an afterthought, especially with JWTs. You need a strategy from the very beginning. A simple token blacklist stored in your database or a cache like Redis is a common and battle tested way to invalidate compromised tokens before they expire.
At the end of the day, the most secure system is the one you understand inside and out. Take the time to really get the tradeoffs. A simple, well understood TokenAuthentication setup is infinitely better than a complex JWT implementation riddled with security holes you did not see coming.Your goal is to build a rock solid foundation that you can extend with confidence as your application grows and evolves.
Building secure, scalable, and maintainable Django applications is what I do best. If you're an early stage startup looking to accelerate your roadmap or strengthen your technical foundations, Kuldeep Pisda can help you navigate these architectural decisions and deliver robust systems. Let's build something great together.
Become a subscriber receive the latest updates in your inbox.



Member discussion