I still remember the feeling. A late night Slack alert, a frantic search through git history, and the cold realization that a .env file had been committed. We have all been there, or at least we have all heard the horror stories. Managing secrets like API keys, database credentials, and certificates feels like a solved problem until it very much is not.
The leap from local development to a shared, secure, and auditable system is a huge one. It's a journey from 'I hope nobody finds this' to 'I know exactly who accessed what, and when.' That one leaked API key a few years back taught me a hard lesson about the critical need for robust security, a principle that applies everywhere, even when understanding self custodial security for digital assets. This guide is that journey, mapped out for you.
We are not just listing options; we are exploring the tradeoffs I have weighed in real projects for engineering teams. We will look at the big cloud providers (AWS Secrets Manager, Azure Key Vault), the developer first darlings (Doppler, 1Password), and the enterprise powerhouses (HashiCorp Vault, CyberArk) to find the best secrets management tools for your specific headache. Whether you are a solo developer running a Django app on a single server or a CTO scaling a complex Kubernetes architecture, this article will help you choose the right tool for the job. Each entry includes our honest take on its pros, cons, and ideal use cases, complete with direct links to get you started.
1. AWS Secrets Manager
For teams deeply embedded in the Amazon Web Services ecosystem, AWS Secrets Manager is often the default, and for good reason. It provides a fully managed service that simplifies storing, rotating, and retrieving credentials, API keys, and other secrets throughout their lifecycle. Its core strength lies in its profound, native integration with other AWS services like RDS, Redshift, and ECS, making it one of the most seamless and best secrets management tools for cloud native applications running on AWS.
The service's killer feature is its automated rotation capability for supported services. Imagine your application's database credentials automatically rotating every 30 days without any manual intervention or application downtime. That's the peace of mind Secrets Manager delivers.
Key Considerations & Use Cases
- Best For: Organizations heavily invested in the AWS cloud seeking a "set it and forget it" solution with powerful IAM controls and audit trails via CloudTrail.
- Pricing: Pay per secret per month (around $0.40) and per 10,000 API calls (around $0.05). This model is predictable but can become costly with thousands of secrets or very frequent access.
- Not Ideal For: Multi cloud or hybrid environments where a single, vendor neutral tool is preferred. The reliance on IAM can also be a steep learning curve for teams new to AWS.
My Take: AWS Secrets Manager excels at reducing operational overhead for AWS centric teams. The automatic rotation is a massive security win. However, be mindful of potential vendor lock in and escalating costs as your secret count and regional replication needs grow. Strong IAM policies are critical to ensure least privilege access, a foundational concept in any robust security posture. For a deeper dive into foundational security, explore our guide on data encryption best practices your startup can't ignore.
Website: aws.amazon.com/secrets-manager/
2. Azure Key Vault
For organizations running on Microsoft's cloud, Azure Key Vault is the natural and powerful choice. It's a centralized cloud service for securely storing and accessing application secrets, keys, and certificates. Its greatest advantage is its deep, native integration with the entire Azure ecosystem, from App Services and Virtual Machines to Azure DevOps, making it one of the best secrets management tools for applications built on Azure.
The service truly shines with its comprehensive certificate lifecycle management. Key Vault can handle the entire process of requesting, renewing, and deploying public and private SSL/TLS certificates, a task that often involves significant manual effort. This, combined with its strong integration with Entra ID (formerly Azure AD) for access control, simplifies a critical aspect of application security.
Key Considerations & Use Cases
- Best For: Companies heavily invested in the Azure cloud or with a significant Microsoft technology stack, requiring a single service for secrets, keys, and certificate management.
- Pricing: A pay per transaction model (e.g., per 10,000 operations) plus monthly fees for keys in the Premium tier (HSM backed). This can be cost effective for low traffic applications but harder to forecast for high volume use.
- Not Ideal For: Multi cloud strategies where a single, cloud agnostic tool is needed. The interface and reliance on Azure specific concepts can be a hurdle for teams not already familiar with the platform.
My Take: Azure Key Vault is the go to solution for securing Azure native applications. Its tight integration with Entra ID for granular access control is a major security benefit. However, the operational pricing model requires careful monitoring to avoid unexpected costs. Effective management hinges on a solid understanding of role based access control implementation to ensure applications and users have only the permissions they absolutely need. To get started, explore our guide on a guide to role based access control implementation.
Website: azure.microsoft.com/services/key-vault/
3. Google Cloud Secret Manager
For development teams building on Google Cloud Platform, Google Cloud Secret Manager offers a straightforward, fully managed solution that feels like a natural extension of the GCP ecosystem. Its primary appeal lies in its simplicity and tight integration with Google's Identity and Access Management (IAM) for granular permissions and Cloud Audit Logs for comprehensive tracking. This makes it an excellent choice among the best secrets management tools for securing applications running on services like Google Kubernetes Engine (GKE) or Cloud Run.
A key differentiator is its transparent and developer friendly approach. The service features robust secret versioning, allowing you to pin specific versions of a secret to an application and roll back with ease if needed. Furthermore, its event driven notifications via Pub/Sub enable automated workflows, such as triggering a function to redeploy an application whenever a critical secret is rotated.
Key Considerations & Use Cases
- Best For: Teams committed to the GCP ecosystem who value a clean API, predictable per version pricing, and seamless integration with existing IAM policies and audit logs.
- Pricing: A generous free tier is offered for a small number of secrets and access operations. Beyond that, you pay a small monthly fee per active secret version and a low rate per 10,000 access operations, making costs very transparent and manageable.
- Not Ideal For: Organizations requiring a single secrets management solution across multiple cloud providers or on premises data centers. While possible, using it outside of GCP requires more complex setup and forgoes the native integration benefits.
My Take: Google Cloud Secret Manager is a powerful, no fuss option for GCP native teams. The per versioning model provides excellent control and auditability, a critical feature for compliance and incident response. While it reinforces a GCP centric architecture, its simplicity and strong security primitives make it a top contender for anyone building seriously on Google Cloud.
Website: cloud.google.com/secret-manager
4. HashiCorp Vault (HCP Vault and self managed)
When you need a powerful, platform agnostic solution that can bridge multi cloud, hybrid, and on premises environments, HashiCorp Vault is often the answer. It has become the de facto industry standard for secrets management at scale, offering unparalleled flexibility. Whether you opt for a managed HCP Vault cluster to get started quickly or the self managed Enterprise version for maximum control, it provides a unified interface for securing, storing, and controlling access to tokens, passwords, certificates, and encryption keys.
Vault's standout capability is its dynamic secrets feature. Instead of storing a static database password, Vault can generate unique, temporary credentials on the fly for an application, automatically revoking them after use. This "just in time" access model drastically reduces the risk associated with long lived static credentials, making it one of the best secrets management tools for security conscious organizations.
Key Considerations & Use Cases
- Best For: Large enterprises or startups with complex, multi cloud, or hybrid infrastructure that require a single source of truth for all secrets and advanced security workflows.
- Pricing: Open source is free. HCP Vault is usage based, factoring in clients, secrets, and cluster hours. Enterprise has custom pricing based on features like namespaces and replication.
- Not Ideal For: Small teams needing a simple plug and play solution without the operational overhead. The learning curve for its policy engine and architecture can be steep compared to SaaS only tools.
My Take: Vault is the swiss army knife of secrets management. Its flexibility is its greatest strength but also contributes to its complexity. Getting the security model right requires a deep understanding of its architecture and robust policies. It's a significant investment in time and expertise, but one that pays dividends for organizations that need its power and vendor neutrality. For more on the underlying principles, see how symmetric vs. asymmetric keys are explained.
Website: www.hashicorp.com/products/vault/
5. 1Password (Secrets Management for Devs)
Known primarily for its exceptional consumer and business password manager, 1Password has impressively extended its secure foundation into the developer world. It leverages its best in class user experience to provide a compelling secrets management solution for teams who already trust the platform. Instead of being a ground up, infrastructure focused tool, it's an extension of a product developers might already use daily, making adoption incredibly smooth.
The platform's strength is its human centric approach to a traditionally complex problem. Through features like Service Accounts and the self hosted 1Password Connect server, it allows developers to fetch secrets programmatically in CI/CD pipelines, applications, and infrastructure configurations. This makes it one of the best secrets management tools for teams looking to bridge the gap between human managed credentials and automated, machine to machine secrets.
Key Considerations & Use Cases
- Best For: Teams already using 1Password for Business who want a unified platform for both human and service secrets, especially those valuing a polished user interface and developer experience.
- Pricing: Secrets Automation is included in the 1Password Business plan (around $7.99 per user/month) with additional usage costs for API requests beyond the included allotment.
- Not Ideal For: Organizations seeking a fully open source solution or those needing advanced, infrastructure native features like dynamic secret generation for a wide variety of backend systems.
My Take: 1Password offers a brilliantly accessible on ramp to proper secrets management. The ability to use secret references instead of plaintext values in config files is a huge win for security posture. While it may not replace a tool like Vault for complex, self hosted infrastructure needs, it provides an elegant and secure solution for a massive range of common development workflows. This approach reinforces the core principles of protecting sensitive data, a concept we explore further in our guide on how to securely store passwords in a database.
Website: 1password.com/features/secrets-management
6. Doppler
Doppler positions itself as the "first Universal Secrets Platform," and it lives up to this claim by focusing intensely on the developer experience. It provides a centralized, easy to use dashboard for managing secrets across multiple projects and environments (development, staging, production), making it one of the best secrets management tools for teams that prioritize speed and simplicity without sacrificing security. The core workflow is designed to get you up and running in minutes, not days.
Its main appeal lies in its "it just works" philosophy. With a powerful CLI, extensive integrations with services like Vercel, GitHub Actions, and Kubernetes, and real time secret syncing, Doppler removes the friction often associated with managing application configuration. Developers can fetch the exact secrets they need for any environment with a single command, doppler run -- ..., which injects secrets as environment variables into their application process.
Key Considerations & Use Cases
- Best For: Startups and modern development teams looking for a SaaS solution with an exceptional user interface and a strong focus on developer productivity and CI/CD integration.
- Pricing: Offers a generous free tier for individuals and small teams. Paid plans are user based, starting around $7 per user per month, making it very predictable and scalable as your team grows.
- Not Ideal For: Organizations with strict self hosting requirements or those needing complex, custom automation workflows that might be better served by a more extensible tool like HashiCorp Vault.
My Take: Doppler is a fantastic choice for teams who want to solve secrets management and move on. Its simplicity is its greatest strength, abstracting away complexity and providing a beautiful interface for collaboration. The focus on syncing configs across environments prevents drift and makes onboarding new developers a breeze. While it is a SaaS platform, its thoughtful design and clear pricing make it a compelling and pragmatic solution for most modern software teams.
Website: www.doppler.com/
7. Akeyless Vault Platform
For organizations navigating complex regulatory landscapes or aiming for a multi cloud strategy without vendor lock in, Akeyless presents a compelling modern alternative. It's a SaaS first platform built on a unique zero knowledge cryptography model, ensuring that Akeyless itself can never access customer secrets. This FIPS 140 2 validated approach provides a high level of assurance, particularly for companies in finance, healthcare, and government sectors.
Akeyless stands out by unifying several security functions into one platform. Beyond just secrets management, it extends into privileged access management (PAM), key management (KMS), and certificate lifecycle management (CLM). This consolidation can significantly reduce tool sprawl and simplify security operations, making it one of the best secrets management tools for teams seeking an all in one solution.
Key Considerations & Use Cases
- Best For: Enterprises in regulated industries or those operating in hybrid and multi cloud environments who need a single platform for secrets, keys, certificates, and access management.
- Pricing: Akeyless uses a model based on the number of clients (e.g., applications, servers, containers) and connectors, which can offer predictability but requires careful planning to understand total cost.
- Not Ideal For: Small teams or startups that only need basic secret storage without the overhead of a comprehensive security platform. The feature breadth, while powerful, might be overkill for simpler use cases.
My Take: The zero knowledge architecture of Akeyless is its biggest differentiator, providing a powerful security guarantee that appeals to risk averse organizations. Its ability to offer both a pure SaaS and a hybrid model (with on premises gateways) gives it the flexibility to meet stringent data residency and compliance requirements. While the licensing can seem more complex than per secret models, the platform's unified nature often justifies the investment by replacing multiple disparate tools.
Website: www.akeyless.io/
8. CyberArk Secrets Manager
For organizations where enterprise grade governance and compliance are non negotiable, CyberArk stands as a giant in the Privileged Access Management (PAM) space. Their Secrets Manager solution extends this robust security posture to applications, DevOps pipelines, and cloud native environments. It is designed from the ground up to provide centralized control, strict policy enforcement, and comprehensive audit trails for machine identities, making it one of the best secrets management tools for large, complex, or highly regulated industries.
The platform offers both self hosted and SaaS deployment models, providing flexibility for different infrastructure strategies. A standout feature is the Secrets Hub, which allows organizations to centrally manage and enforce policies even on secrets stored natively in cloud vaults like AWS Secrets Manager or Azure Key Vault, offering a single pane of glass for security teams.
Key Considerations & Use Cases
- Best For: Large enterprises, financial services, and healthcare organizations that require extensive auditing, compliance reporting (SOX, PCI, etc.), and integration with a broader identity security platform.
- Pricing: Enterprise focused and quote based. It is positioned as a premium solution, which may place it out of reach for smaller startups or teams without significant compliance drivers.
- Not Ideal For: Small teams or startups seeking a simple, low cost, or developer first solution. The comprehensive feature set can introduce complexity that is unnecessary for less demanding use cases.
My Take: CyberArk is the heavyweight champion for enterprise secrets management, especially when secrets are part of a larger identity security and PAM strategy. The ability to manage other cloud providers' vaults is a powerful feature for multi cloud governance. However, this power comes at a premium price and with a complexity that requires dedicated security team involvement. If your CISO needs detailed audit logs and centralized policy across every environment imaginable, CyberArk is a top contender.
Website: www.cyberark.com/products/secrets-management/
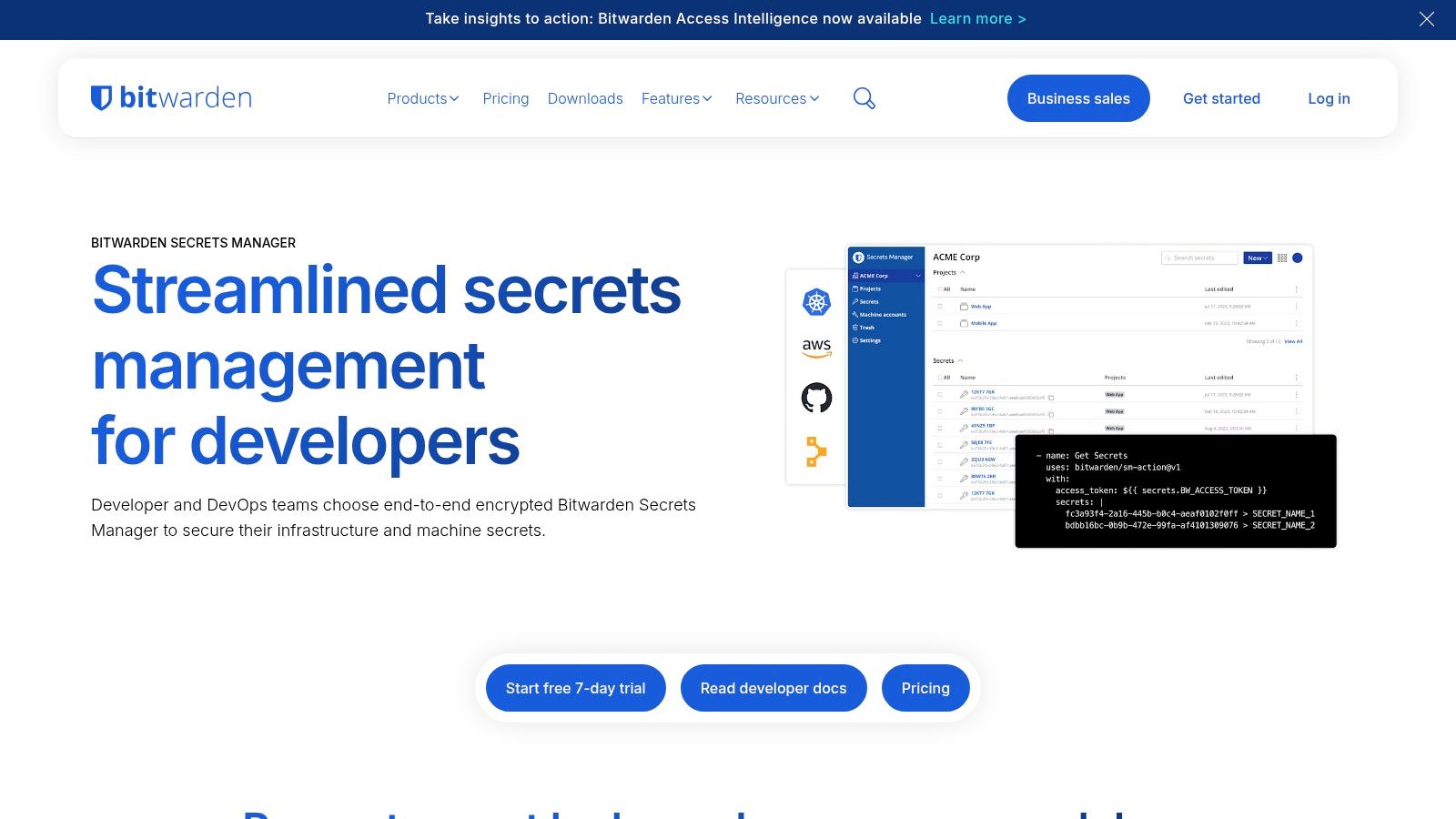
9. Bitwarden Secrets Manager
For teams already using and trusting Bitwarden for password management, their Secrets Manager is a natural and highly logical extension. It leverages the company's open source pedigree to offer a developer focused solution for managing application secrets like API keys, database credentials, and certificates. Its core appeal is its simplicity, transparency, and an extremely accessible pricing model that disrupts the often high cost of enterprise grade tooling.
This makes it one of the best secrets management tools for startups, small to medium sized businesses, or any cost conscious organization. The seamless integration between human focused password management and machine focused secrets management within a single ecosystem streamlines security operations and procurement.
Key Considerations & Use Cases
- Best For: Cost conscious teams, existing Bitwarden customers, and organizations that value open source and the option for self hosting. Its free tier is very generous for individuals and small projects.
- Pricing: Offers a free plan for two users and two projects. Paid team plans start around $6 per user per month, providing an affordable entry point for growing teams.
- Not Ideal For: Enterprises needing advanced, out of the box dynamic secrets capabilities or complex automated workflows that are more mature in platforms like Vault or the major cloud providers.
My Take: Bitwarden Secrets Manager is a formidable contender, especially for its price point and open source nature. It democratizes secrets management, making robust security accessible to teams without massive budgets. The developer experience is solid with a capable CLI and SDKs. While it may lack the bells and whistles of more expensive solutions, it perfectly covers the essential needs for a huge segment of the market.
Website: bitwarden.com/products/secrets-manager/
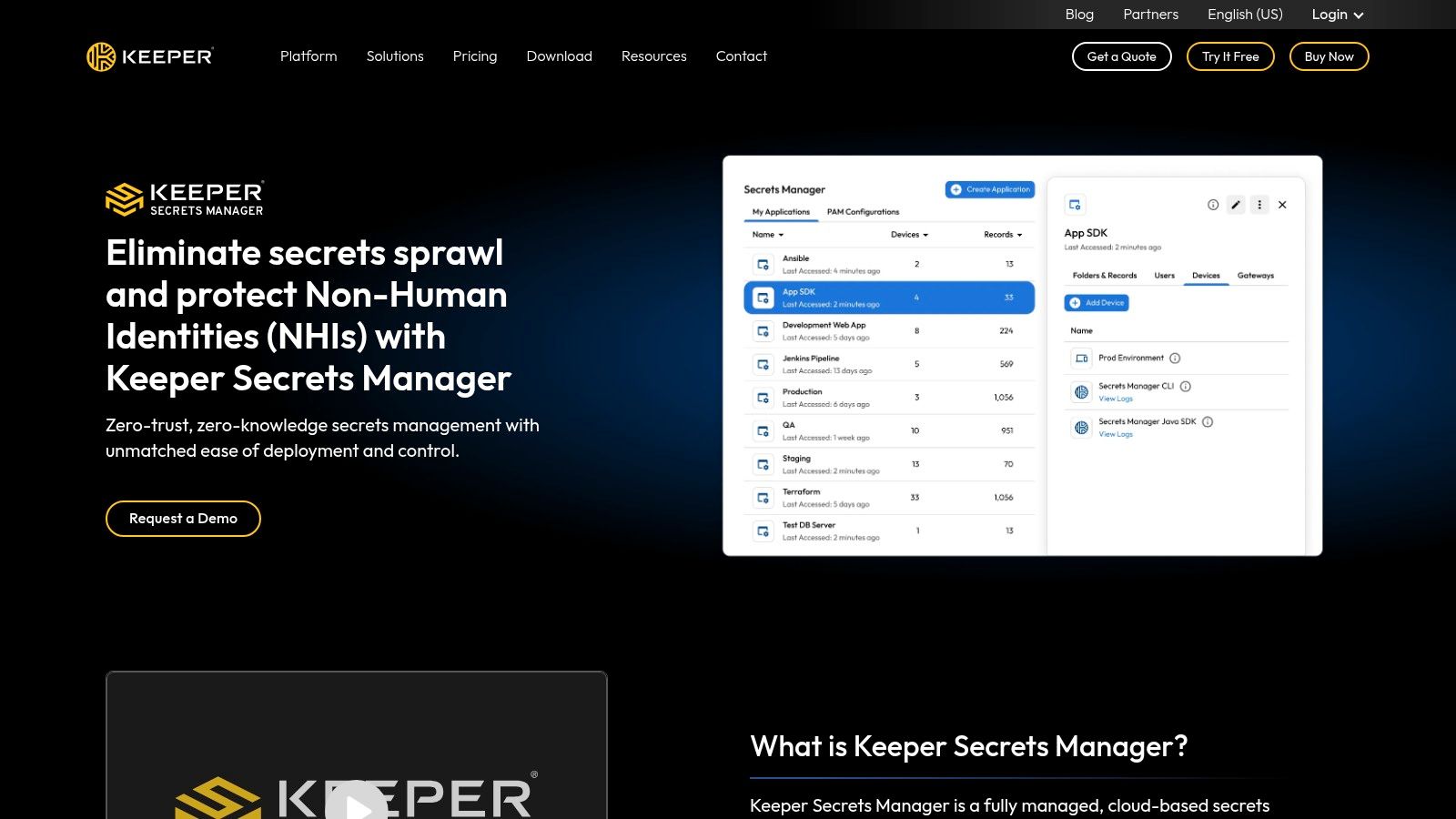
10. Keeper Secrets Manager
For organizations already leveraging Keeper's well regarded password manager and privileged access management (PAM) platform, Keeper Secrets Manager is a natural and powerful extension. It brings the company's signature zero knowledge security architecture to the DevOps and CI/CD world, providing a cloud hosted solution for infrastructure secrets like API keys, database credentials, and certificates. Its main appeal is creating a unified security plane for both human and machine secrets.
This integration within the broader KeeperPAM platform means developers and security teams operate from a single, familiar admin console. This simplifies policy enforcement, role based access control (RBAC), and SIEM integration, making it one of the best secrets management tools for companies seeking to consolidate their security stack and reduce vendor sprawl.
Key Considerations & Use Cases
- Best For: Companies already invested in the Keeper ecosystem or those looking for a single platform that combines password management, privileged access, and infrastructure secrets management with a strong zero knowledge security model.
- Pricing: Secrets Manager is sold as an add on to the Keeper Business or Enterprise plans. Pricing is not transparently listed online and typically requires engaging with their sales team for a custom quote based on usage and features.
- Not Ideal For: Teams seeking a standalone, open source, or self hosted solution. The pricing model and requirement for a base Keeper plan may not suit startups or developers looking for a simple, low cost entry point.
My Take: Keeper Secrets Manager is an excellent choice for organizations aiming for security stack consolidation. The unified admin and strong zero knowledge foundation are compelling. The ability to manage secrets rotation for databases, SSH keys, and cloud services directly from the platform reduces operational complexity. However, the opaque, sales driven pricing model is a significant drawback for teams that prefer self service and predictable, transparent costs.
Website: https://www.keepersecurity.com/secrets-manager.html
11. IBM Cloud Secrets Manager (powered by HashiCorp Vault)
For enterprises operating within the IBM Cloud ecosystem or those requiring stringent compliance and data residency controls, IBM Cloud Secrets Manager offers a compelling solution. This service is essentially a single tenant, dedicated instance of HashiCorp Vault, managed by IBM. It combines the battle tested power and flexibility of Vault with the integration and compliance framework of the IBM Cloud, making it one of the best secrets management tools for regulated industries.
The core advantage here is single tenancy, which provides strong workload isolation and predictable performance. It's designed for organizations that need to centralize secrets management while integrating deeply with IBM services like Key Protect for bring your own key (BYOK) capabilities and Identity and Access Management (IAM) for granular access control.
Key Considerations & Use Cases
- Best For: Highly regulated industries (finance, healthcare) and existing IBM Cloud customers who need a dedicated, compliant, and integrated Vault instance without the overhead of self hosting.
- Pricing: A free trial tier is available. Standard pricing is based on a per instance and per user model, starting around $500 per month for an instance plus additional costs per authorized user.
- Not Ideal For: Startups, multi cloud first teams, or those on a tight budget. The ecosystem is smaller compared to the big three cloud providers, which might limit out of the box integrations with non IBM services.
My Take: IBM Cloud Secrets Manager successfully carves out its niche by offering the power of Vault within a managed, single tenant, and highly compliant package. It's an excellent choice for enterprises that prioritize isolation and are already committed to the IBM Cloud platform. However, the cost and IBM centric focus make it less suitable for smaller companies or those seeking a more cloud agnostic solution.
Website: www.ibm.com/products/secrets-manager
12. AWS Marketplace (Secrets Management listings)
Instead of being a single tool, AWS Marketplace is a curated digital catalog that simplifies finding, buying, and deploying third party secrets management tools directly within your AWS environment. For teams that want specialized solutions beyond AWS Secrets Manager but need to streamline procurement, this is an invaluable resource. It centralizes billing, standardizes contracts, and often provides one click deployment options for popular platforms like Akeyless or Infisical.
This approach combines the flexibility of choosing from many of the best secrets management tools with the operational convenience of the AWS ecosystem. Imagine getting consolidated billing for your entire cloud stack, including your third party secrets manager, all on your single AWS invoice. That's the core value proposition here, especially for larger organizations with complex procurement cycles.
Key Considerations & Use Cases
- Best For: US based AWS customers who want a specialized, non native secrets manager but need to simplify procurement, vendor management, and billing through their existing AWS account.
- Pricing: Varies entirely by the vendor and their specific listing. Can be SaaS subscriptions, Bring Your Own License (BYOL) models, or usage based pricing, all processed via AWS.
- Not Ideal For: Teams operating outside the AWS ecosystem or those looking for a single, direct relationship with a tool vendor without an intermediary.
My Take: Think of AWS Marketplace as a strategic procurement shortcut. It's a fantastic way to acquire powerful, specialized tools while avoiding the headache of onboarding new vendors. You gain access to a wide selection of solutions and can leverage enterprise features like private offers for custom pricing. The primary limitation is that it's a facilitator, not a tool itself, so you're still responsible for evaluating the underlying security and features of each vendor's product.
Website: aws.amazon.com/marketplace
Top 12 Secrets Management Tools Comparison
| Product | Core features | Best for | Unique selling point | Pricing note |
|---|---|---|---|---|
| AWS Secrets Manager | Automatic rotation; IAM & CloudTrail auditing; cross Region replication | AWS centric startups & services | Native AWS integrations and enterprise scale | Per secret + API calls; costs scale with versions/regions |
| Azure Key Vault | Secrets, keys (HSM), certificates; RBAC/Entra ID | Microsoft/Azure heavy stacks | HSM and certificate lifecycle + Azure DevOps tie ins | Operation based pricing; Premium for HSM features |
| Google Cloud Secret Manager | Versioned secrets; IAM & audit logs; Pub/Sub rotation | GCP teams and developer friendly apps | Transparent per version pricing and clean APIs | Per secret/version pricing; free tier available |
| HashiCorp Vault (HCP/self managed) | Static/dynamic/ephemeral secrets; policies; replication/DR | Multi cloud, hybrid, on prem at scale | Vendor neutral, highly flexible secret engines | OSS self managed; Enterprise/HCP paid tiers for features |
| 1Password (Secrets for Devs) | Service accounts; Connect bridge; CI/CD integrations | Teams already on 1Password adopting secrets in pipelines | Excellent UX and developer tooling for secrets in workflows | Subscription based; not open source; Connect self hosted only |
| Doppler | Central workspace/envs; auto rotation; CLI/SDKs | Developer teams wanting fast setup and sync | Fast onboarding, clear team workflows and tooling | User based pricing; clear public plans (Enterprise add ons) |
| Akeyless Vault Platform | SaaS/hybrid with gateways; zero knowledge crypto; CLM/KMS/PAM | Regulated, hybrid/multi cloud enterprises | Zero knowledge security + hybrid deployment options | Complex licensing (clients/connectors); enterprise pricing |
| CyberArk Secrets Manager | Centralized rotation/policy; DevOps integrations; Secrets Hub | Large enterprises with strict governance/compliance | Strong PAM governance and identity platform integration | Quote based, enterprise level pricing (premium) |
| Bitwarden Secrets Manager | Secrets vault; CLI/SDK; optional self hosting | Cost conscious teams and Bitwarden users | Open source aligned; low cost and transparent | Free tier + paid tiers; self hosting available on higher plans |
| Keeper Secrets Manager | RBAC & SIEM integrations; automated rotation; CLI/SDK | Organizations standardizing on Keeper/PAM | Zero knowledge model with PAM integrations | Sold as add on; pricing usually quoted via sales |
| IBM Cloud Secrets Manager (Vault based) | Dedicated Vault instance; PKI/HSM support; logging | IBM Cloud customers and regulated workloads | Single tenant isolation and IBM compliance features | IBM Cloud pricing; enterprise/regulated focus |
| AWS Marketplace (Secrets listings) | One click SaaS/AMI procurement; private offers; consolidated billing | AWS customers buying third party secrets tools | Simplifies procurement, billing and trials for AWS users | Vendor specific pricing and terms via marketplace listings |
So, Which Tool Gets Your Secrets?
We have journeyed through a landscape filled with powerful contenders, each offering a unique approach to safeguarding your most sensitive data. From the native convenience of AWS Secrets Manager and Google Cloud Secret Manager to the unparalleled control of a self hosted HashiCorp Vault, the options can feel overwhelming. We have seen how tools like Doppler and 1Password are laser focused on developer experience, aiming to make security seamless, while platforms like Akeyless and CyberArk cater to enterprise grade compliance and control.
The central truth is this: there is no single "best" secrets management tool for everyone. The right choice is deeply contextual, tied to your team's existing workflow, technical stack, and operational maturity. Chasing the most feature rich option can sometimes lead to a solution so complex that your team avoids it, defeating the entire purpose. The "perfect" system is the one that gets adopted, used consistently, and makes the secure path the easiest one to follow.
Your Roadmap to Choosing a Secrets Management Tool
So, how do you move from analysis to action? Let's distill our journey into a practical decision making framework. Before you commit, pause and reflect on these core questions with your team:
- What is your "center of gravity"? Are you a single cloud native team, deeply embedded in AWS, Azure, or GCP? If so, the path of least resistance is often the native tool. The tight integration with IAM roles and other cloud services is a massive operational advantage.
- How complex is your ecosystem? As your infrastructure grows, especially with patterns like a microservices architecture, the need for a central, platform agnostic source of truth becomes critical. This is where tools like HashiCorp Vault, Doppler, or Akeyless begin to shine, offering a unified control plane across disparate environments.
- Who are the primary users? If your main goal is to empower developers to manage application secrets in CI/CD pipelines and local development, prioritize developer experience. Look at Doppler's slick CLI, 1Password's intuitive UI, or Bitwarden's simplicity. If auditors and security teams are the primary stakeholders, then robust audit logs, granular access policies, and compliance certifications from CyberArk or Akeyless become paramount.
- What is your operational capacity? Be honest about your team's ability to manage infrastructure. A self managed HashiCorp Vault instance is incredibly powerful, but it is also a complex, stateful service that requires dedicated expertise to run reliably. Managed offerings like HCP Vault or fully SaaS platforms like Doppler offload this burden entirely, letting you focus on using the tool, not maintaining it.
Ultimately, selecting one of the best secrets management tools is a pivotal step in building a resilient and secure engineering culture. It is not just a technical decision; it is an investment in your team's velocity and your product's integrity. Start with your biggest, most immediate pain point, whether it is rotating database credentials, securely injecting secrets into Kubernetes, or simply getting .env files out of your Git repositories. Solve that problem first. The momentum you gain will illuminate the path forward. Your secrets are counting on it.
Navigating these architectural decisions can be daunting, especially when you are balancing security, cost, and developer productivity. If you are wrestling with this choice and need a strategic sounding board, I offer consulting and code audits through Kuldeep Pisda. Let us build a secure, scalable foundation for your next big thing. Learn more at Kuldeep Pisda.
Become a subscriber receive the latest updates in your inbox.


Member discussion