
Remember the bustling living room at Pied Piper headquarters from HBO’s hit show Silicon Valley. A modest crowd of scrappy developers huddle around a single laptop, eyes widened in disbelief. Their newly-created AI has just cracked an impenetrable encryption protocol—something that was supposed to take millions of years—in mere seconds. Lines of encrypted data morph into plain text, and as realization dawns, their triumphant expressions freeze into a collective look of dread.
Sound familiar? It’s that lightbulb moment where fantasy meets reality. When that episode aired, it felt like pure sci-fi. But fast-forward to today, and thanks to advances in quantum computing—highlighted by Microsoft’s groundbreaking “Majorana” quantum chip—we might be inching closer to a world where such scenarios are no longer reserved for Hollywood scripts.
Why Cryptography Matters?
To appreciate the gravity of quantum computing’s threat, it helps to understand how cryptography underpins our modern digital world.
Lock and Key
Think of cryptography like a lock on a door. You secure your house with a lock (i.e., encryption algorithm) and keep the key to yourself. The other person you trust also has a matching key so they can unlock it. Anyone else who tries to open the door (i.e., decrypt your message) would need an astronomical amount of time to “guess” the key by brute force—effectively making it infeasible.
Mathematical Puzzles
Many encryption techniques (e.g., RSA, Elliptic Curve Cryptography) rely on math puzzles such as factoring large numbers. For classical computers, factoring something like a 2048-bit RSA key is so computationally intensive that it’d take eons to solve. So, for the moment, your locked “door” is secure.
The Brute-Force Barrier
Right now, the reason encryption stands strong is because brute-forcing large keys requires near-infinite resources on classical machines. It’s like trying every single possible combination of a 100-digit lock—on a standard computer, that’s effectively impossible within any reasonable lifetime.
Quantum computing flips this on its head. Instead of trying one key at a time, a quantum machine can (conceptually) examine many possibilities at once. If we had a powerful enough quantum computer, that “infinite” time shrinks dramatically, and previously unbreakable locks start popping open.
Quantum Computers!!!
Bits vs. Qubits
Classical computers run on bits—0s and 1s—like switches that are off (0) or on (1). Quantum computers, by contrast, use qubits, which can exist in both states simultaneously, a property called superposition. This allows them to process a vast number of calculations in parallel.
Another critical quantum phenomenon is entanglement, enabling qubits that are physically separate to be deeply connected in how they behave. Combined, superposition and entanglement give quantum computers the potential to outpace classical machines for certain tasks—most notably, the mathematical ones that underpin our current encryption systems.
Classical Bits
Classical computers use bits that can only be in one state at a time - either 0 (off) or 1 (on). Click the bits below to toggle their states:
Quantum Superposition
Qubits can exist in multiple states simultaneously, thanks to quantum superposition. The spinning effect below represents this quantum property:
Quantum Entanglement
When qubits become entangled, their states become correlated in a way that has no classical counterpart. Click the button to see how changing one entangled qubit affects the other:
The “Majorana” Chip: Microsoft’s Leap Forward
Microsoft recently unveiled a quantum chip they’ve dubbed “Majorana”, named for Majorana fermions—exotic particles that could help build more topologically stable qubits. These qubits, often called “topological qubits,” are theorized to be more resistant to outside interference (noise), which is a huge problem for quantum computers. Noise can collapse a qubit’s delicate quantum state, causing errors.
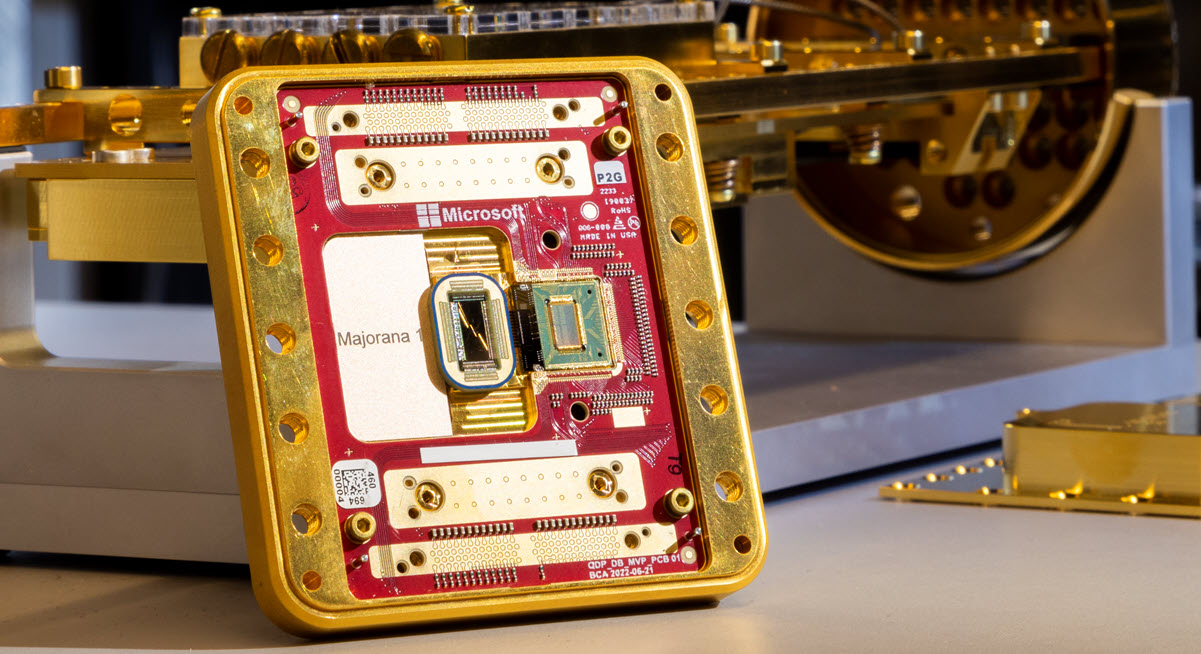
By using these Majorana fermions, Microsoft aims to create a system that stays stable longer, thus handling more complex computations without error. If successful, it marks a major stride toward scaling quantum computers—and scaling is precisely the missing piece before quantum machines can attempt big tasks like breaking RSA or ECC keys.
As soon as a quantum machine reaches a sufficient “qubit count” and stability, it could, in theory, solve the factoring of large numbers exponentially faster. That’s when all the modern cryptography we rely on today becomes fragile.
The Looming Quantum Threat to Cryptography
Why RSA and ECC Are Vulnerable
Two of the most commonly used cryptographic algorithms are RSA (Rivest–Shamir–Adleman) and ECC (Elliptic Curve Cryptography). Here’s why they’re particularly at risk:
- RSA: Based on the difficulty of factoring very large numbers.
- ECC: Based on the discrete logarithm problem within elliptic curves.
Classical computers find both tasks extremely challenging if the key sizes are large enough. Shor’s Algorithm, discovered by mathematician Peter Shor, showed that a sufficiently large quantum computer could factor large numbers exponentially faster than classical machines. This means RSA’s entire security premise would crumble, taking ECC down with it in a similar fashion.
Understanding Shor's Algorithm
Watch how Shor's algorithm uses quantum superposition and period finding to factor large numbers.
Harvest Now, Decrypt Later
The threat isn’t just about future transactions. Attackers may be recording encrypted data right now, with the plan to hold onto it until quantum computers become powerful enough to decrypt everything. This tactic is referred to as “harvest now, decrypt later.” Sensitive information like financial data, health records, or intellectual property typically needs to remain private for decades—so if it’s stolen today, it could be deciphered in a quantum future.
Recent Research and Warnings
Academic and industry research has steadily highlighted these dangers:
- A 2024 paper in the Frontiers in Physics journal underscores how Quantum Key Distribution (QKD) is already being explored to keep encryption keys secure 99.
- Another recent study notes that public key cryptography—RSA, ECC, and DH (Diffie-Hellman)—are particularly vulnerable because quantum machines can tackle the core math problems behind these algorithms.
Meanwhile, cybersecurity experts like Dr. Michele Mosca (CEO of evolutionQ) and Dr. Jason Sabin (CTO at DigiCert) consistently warn that now is the time for organizations to prepare for the inevitable rise of quantum attacks.
A Closer Look at Microsoft’s Majorana Chip

Topological Qubits, Simplified
What sets Microsoft’s Majorana chip apart is its focus on topological qubits. Imagine your qubits are fragile figurines on a shaky table—any vibration could knock them over. In quantum computing, “vibration” comes from random environmental noise. One bump, and your qubit’s quantum state is gone.
Topological qubits aim to “anchor” this figurine more securely, making it harder to knock over. They do this by spreading the quantum information across multiple, special points called Majorana zero modes. The math here is complex, but conceptually, it’s like weaving your qubit into a sturdy knot; small perturbations won’t easily unravel it.
Why the Majorana Chip Matters
- Higher Stability: Reduces errors, meaning you don’t need as many qubits with complex correction mechanisms.
- Scalability: If each qubit is more robust, you can string more of them together before the system becomes unmanageable.
- Real-World Impact: From factoring large numbers to simulating new molecules, a stable quantum chip opens up doors previously considered purely theoretical.
Microsoft’s announcement suggests they are making tangible strides in qubit stability. Although it’s not a fully-fledged quantum supercomputer yet, it’s a sign that quantum hardware is moving from the realm of “maybe someday” to “soon enough to worry about.”
Privacy, Finance, and More
When you think of cryptography, you might picture top-secret government cables. But in reality, strong encryption underpins just about everything online:
- Banking & Finance: Every time you log into your bank or trade stocks, RSA or ECC ensures secure transactions.
- Secure Messaging: Apps like Signal, WhatsApp, or enterprise solutions rely on end-to-end encryption.
- Digital Signatures & Authentication: Your company’s VPN, software updates from major vendors, and even cryptocurrency transactions depend on digital signatures.
- Healthcare & Government: Sensitive patient records, defense communications—an entire layer of trust depends on encryption.
A quantum computer powerful enough to break RSA or ECC doesn’t just mean your chat logs are at risk. It means entire industries could be compromised. Intellectual property theft, espionage, and financial fraud could become child’s play if quantum decryption becomes accessible to bad actors—state-sponsored or otherwise.
Post-Quantum Cryptography
In response to the quantum threat, researchers worldwide are developing post-quantum or quantum-resistant cryptographic algorithms. Unlike RSA or ECC, these new algorithms are built on math problems that even quantum machines shouldn’t be able to solve feasibly.
Types of Post-Quantum Algorithms
- Lattice-Based Cryptography
- Key Ideas: The difficulty of finding short vectors in high-dimensional lattices.
- Example: Kyber (selected by NIST for key encapsulation).
- Why It’s Secure: Quantum computers, as far as we know, can’t easily solve these lattice problems.
- Code-Based Cryptography
- Key Ideas: Using error-correcting codes to form a hard problem.
- Example: McEliece, which has survived decades of cryptanalysis.
- Why It’s Secure: Attacking these codes at scale remains impractical, even for quantum algorithms.
- Multivariate Polynomial Cryptography
- Key Ideas: Solving systems of polynomial equations with multiple variables.
- Example: UOV (Unbalanced Oil and Vinegar) and Rainbow schemes.
- Why It’s Secure: Although partially broken in some configurations, robust variants still stand.
- Hash-Based Signatures
- Key Ideas: Creating signature schemes from well-established hash functions.
- Example: XMSS (eXtended Merkle Signature Scheme).
- Why It’s Secure: Relies on hash functions believed to be resistant to quantum attacks.
The NIST Standards
In August 2024, the U.S. National Institute of Standards & Technology (NIST) set the foundation by announcing the world’s first post-quantum cryptography standards. Algorithms like CRYSTALS-Kyber (for key encapsulation) and CRYSTALS-Dilithium (for digital signatures) have already been selected for standardization.

This is a monumental step, as it gives organizations a clearer roadmap for upgrading their systems. It also encourages hardware and software providers to start implementing and testing these new algorithms sooner rather than later.
Real-World Pilot Programs
Far from being purely academic, post-quantum cryptography is already seeing pilot tests across multiple industries:
- Telecommunications: SK Telecom partnered with Samsung to develop the Galaxy Quantum2 smartphone featuring quantum cryptography. They’re also experimenting with QKD (Quantum Key Distribution) in their infrastructure.
- Shipbuilding & Defense: Hyundai’s shipyard uses quantum cryptography to protect its defense tech. In a world where warship designs or submarine specs are top-secret, quantum-safe communication is mission-critical.
- Network Infrastructure: Verizon conducted a QKD trial in Washington D.C., becoming one of the first major U.S. carriers to test quantum-safe solutions.
- Financial Sector: Major banks are investigating or funding quantum-safe encryption research, focusing on cryptographic upgrades that can protect massive volumes of transaction data.
- Mobile Security: Thales tested end-to-end encrypted phone calls using hybrid cryptography (classical + quantum-safe) to future-proof communications.
These early forays signal that the shift toward post-quantum cryptography is already underway—and not just in top-secret government labs. Industry giants recognize the threat and are acting preemptively.
Should We Be Worried Right Now?
Balancing Fear and Reality
On one hand, quantum computing breakthroughs—like Microsoft’s Majorana chip—are exciting but don’t immediately spell doom for classical encryption. Fully scalable quantum machines are still in the prototype stage. Issues such as error rates, qubit stability, and sheer manufacturing complexity prevent quantum computers from factoring large numbers overnight.
On the other hand, some experts—like Bill Gates—suggest that “useful quantum computers” might be just a few years away. Others, like Nvidia CEO Jensen Huang, speculate it could be 15 to 30 years before we see quantum systems with significant real-world impact. The reality probably lies somewhere in between, but it’s important to note that this timeline can shrink rapidly if any unexpected breakthrough occurs.
The “Store Now, Decrypt Later” Risk
Even if it takes decades before quantum supremacy arrives, the danger posed by harvest now, decrypt later strategies is immediate. If your sensitive data must remain confidential for 20, 30, or 50 years, you cannot ignore the potential for that data to be cracked open in the future. By then, it’s too late to roll out a fix.
The Global Push Toward Quantum Readiness
Governments, tech giants, and cybersecurity firms are not sitting idle:
- NIST is finalizing post-quantum standards.
- ETSI (European Telecommunications Standards Institute) is publishing guidelines for quantum-safe migration.
- China, IBM, Google, and many others are investing heavily in quantum computing and quantum-safe cryptography, with some exploring advanced QKD networks already.
The consensus? Start preparing now. This doesn’t mean a frantic overhaul of everything overnight, but a measured transition strategy called “crypto-agility.”
Crypto-Agility and Migration Strategies
What Is Crypto-Agility?
Crypto-agility means designing your organization’s systems and infrastructure in a way that you can swap out cryptographic algorithms without tearing everything down. If you’re agile, migrating from RSA to a post-quantum algorithm can be more like upgrading a piece of software rather than rebuilding your entire tech stack.
Steps to Prepare
- Inventory Your Cryptographic Assets
Figure out where and how your organization uses encryption. This can include servers, devices, IoT sensors, code repositories, etc. - Risk Assessment
Determine which data is most critical, especially information with a long confidentiality shelf life (e.g., patents, personal records). - Follow NIST and Other Standards
Keep track of standards from NIST, ETSI, and other bodies. Adopt approved algorithms once they are standardized. - Hybrid Cryptography
Use a combination of classical and quantum-resistant algorithms simultaneously. If one is broken, the other is likely to remain secure. - Pilot Programs
Test small-scale deployments of post-quantum algorithms to identify performance impacts and potential issues. - Educate and Train
Ensure your development, security, and IT teams understand the basics of post-quantum cryptography so they can implement it properly.
Looking Toward the Future
Timelines and Tech Realities
“Quantum supremacy” is the term coined to describe the point at which a quantum computer can perform a task that a classical machine simply cannot manage within any reasonable timeframe. While prototypes have hinted at narrow cases of quantum supremacy, applying that power to break real-world encryption is a far more complicated proposition.
Still, the Majorana chip underscores that quantum hardware is evolving at a brisk pace. As these developments pile up, the window for adopting post-quantum solutions narrows. Think of it like climate change: you can’t wait until the ocean is at your doorstep to start building your seawall.
Societal and Ethical Considerations
Beyond the purely technical aspects, there’s a broader societal and ethical dimension to quantum computing. If quantum machines become available to only a few world powers or major corporations, it could significantly reshape the balance of cybersecurity, privacy rights, and intellectual property protection.
- Privacy: How do we safeguard individual rights in a world where encryption might be broken?
- Global Inequality: Countries or companies with quantum access could have a massive intelligence edge.
- Regulations: Expect new legislation about “quantum-safe” standards, export controls on quantum hardware, and data protection laws.
Organizations like the World Economic Forum are already discussing these issues, highlighting the need for transparency, ethical governance, and global cooperation.
Conclusion
We began with a fictional scene from Silicon Valley—Pied Piper’s AI cracking encryption in a snap. Yet, as you’ve seen, the gulf between Hollywood plotlines and real-life technology is narrowing. Microsoft’s Majorana chip is only the latest signpost on the road to scalable quantum computing, and it serves as a clarion call for anyone relying on classical cryptography.
- Quantum Threat is Real, But Not Immediate: Quantum computers powerful enough to break RSA and ECC aren’t here yet. But they’re closer than ever before, thanks to breakthroughs in qubit stability and topological computing.
- Research and Standards Are Ramping Up: Organizations like NIST have already finalized their first post-quantum standards. Governmental bodies, tech giants, and cybersecurity firms are proactively building quantum-safe solutions.
- Harvest-Now, Decrypt-Later Is a Ticking Clock: Even if quantum decryption remains a decade away, sensitive data is already being harvested. Long-term protection demands adopting quantum-resistant methods sooner rather than later.
- Crypto-Agility is Essential: The key takeaway for businesses is to build flexible systems that can swap encryption algorithms without major disruption. This ensures a smoother, faster transition when quantum-safe cryptography reaches standard usage.
- Stay Informed and Proactive: The worst move is apathy. Keep tabs on quantum computing developments, ensure your security teams are aware of post-quantum solutions, and begin pilot projects to get hands-on experience.
In the end, quantum computing is a testament to human ingenuity—an astonishing leap that might help us solve everything from climate modeling to drug discovery. But like any powerful tool, it also brings new risks. The good news is that, with awareness and preparation, we can harness quantum’s potential without sacrificing the digital trust and security that keeps our world running.
So the next time someone mentions Pied Piper’s AI cracking encryption in a TV show, remember: it might not be fiction forever. The responsible step is to start planning for the day when quantum-based reality catches up to Silicon Valley’s imagination. And if we do it right, we won’t be caught off guard when that day arrives.
Reads
- Microsoft’s Majorana quantum computer chip
- Infosecurity Magazine on Microsoft’s quantum chip and encryption
- Study on public key cryptography vulnerabilities (2024)
- Security Week: Quantum and the threat to encryption
- World Economic Forum on quantum computing & encryption (2024/08)
- NIST Post-Quantum Standards Initiative
- First four quantum-resistant cryptographic algorithms (Embedded.com)
- Akitra’s overview of quantum-resistant cryptography
- Frontiers in Physics – Quantum Key Distribution research
- “Harvest now, decrypt later” discussion at CIO.inc
- DigiCert’s CTO on PQC solutions
- Timeline of quantum computing and communication (Wikipedia)
- Bill Gates’ quantum computer predictions (Quantum Insider)
- SK Telecom and Samsung’s Galaxy Quantum2 phone with QKD
- Thales post-quantum call pilot
Become a subscriber receive the latest updates in your inbox.






Member discussion